Nix Podman Stacks
Collection of opinionated Podman stacks managed by Home Manager.
The goal is to easily deploy various self-hosted projects, including a reverse proxy, dashboard and monitoring setup. Under the hood rootless Podman (Quadlets) will be used to run the containers. It works on most Linux distros including Ubuntu, Arch, Mint, Fedora & more and is not limited to NixOS.
The projects also contains integrations with Traefik, Homepage, Grafana and more. Some examples include:
- Enabling a stack will add the respective containers to Traefik and Homepage
- Enabling CrowdSec or Authelia will automatically configure necessary Traefik plugins and middlewares
- When stacks support exporting metrics, scrape configs for Prometheus can be automatically set up
- Similariy, Grafana dashboards for Traefik, Blocky & others can be automatically added
- and more ...
Disabling any of those options will of course also remove all associated configurations and containers.
While most stacks can be activated by setting a single flag, some stacks require setting mandatory values, especially for secrets. For managing secrets, projects such as sops-nix or agenix can be used, which allow you to store your secrets along with the configuration inside a single Git repository.
📔 Option Documentation
Refer to the documentation for a full list of available options.
There is also an Option Search to easily explore existing options.
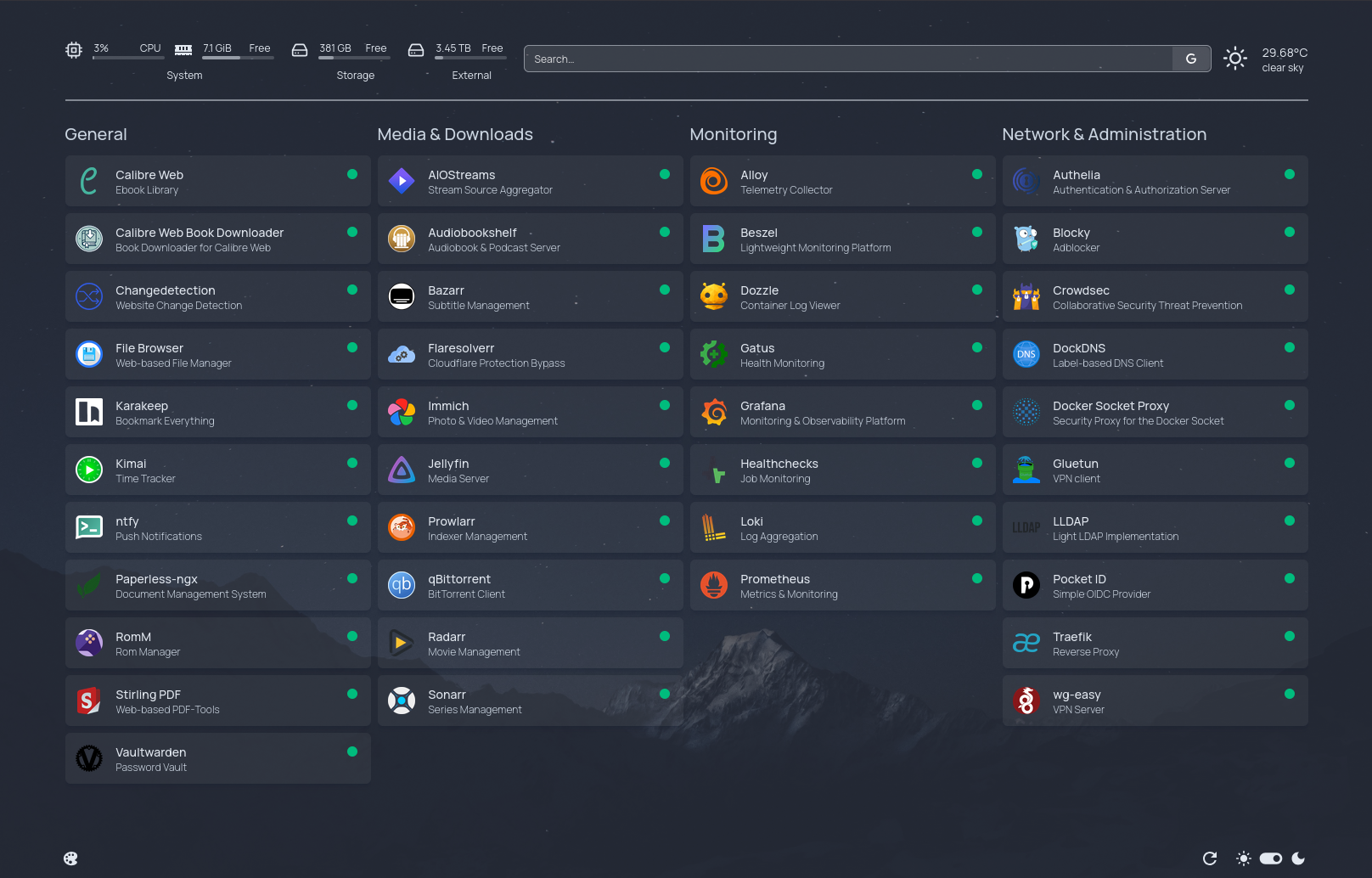
📦 Available Stacks
-
Calibre-Web Automated
 Calibre-Web Automated Book Downloader
Calibre-Web Automated Book Downloader
-
Changedetection
Sock Puppet Browser
-
Alloy
Grafana
Loki
Prometheus
Alertmanager
Alertmanager-ntfy
Podman Metrics Exporter
-
Paperless-ngx
- 📂 FTP Server
-
Bazarr
Flaresolverr
Gluetun
Jellyfin
Prowlarr
qBittorrent
Radarr
Sonarr
⚙️ Prerequisites
- Nix Installation
net.ipv4.ip_unprivileged_port_start=0or any other way of allowing non-root processes to bind to ports below 1024
🚀 Setup
If you already have an existing flake setup, add this projects flake as an input and include the flake output homeModules.nps in your Home Manager modules.
If you don't use Nix yet, you can use the projects template to get started:
nix flake init --template github:Tarow/nix-podman-stacks
Make sure to go through the flake.nix, stacks.nix & sops.nix files and adapt options as needed.
Also make sure to generate your own encryption age key and encrypt your secrets with it!
To apply your configuration, run:
nix run home-manager -- switch --experimental-features "nix-command flakes pipe-operators" -b bak --flake .#myhost
The template includes an example configuration of the following setup:
- Authelia as an OIDC provider with LLDAP as the user backend
- Immich & Paperless with OIDC login pre-configured
- Traefik as a reverse proxy including a Geoblocking middleware. Wildcard certificates will be fetched from Let's Encrypt (DNS Challenge).
- CrowdSec including a Traefik middleware setup
- Blocky as DNS proxy
- Monitoring stack with Alloy, Loki, Grafana & Prometheus. Comes with Grafana dashboards for Traefik & Blocky
- All services are added to the Homepage dashboard
- Podman Socket Access through a read-only proxy
- Secrets are provisioned by sops-nix
A basic overview of the templates architecture will look like this:

🔧 Customize Settings
The Podman stacks are mostly opinionated and configured to work out of the box. Refer to option documentation or the source code of each module to see which options are exposed on stack level and can be modified. An example would be Traefik, which requires a domain to be set. Also it ships with preconfigured static and dynamic configurations, but allows you to extend or customize those.
If the exposed options are not enough, you can always refer to the container definition directly by using the nps.stacks.<stackname>.containers.<containername> options.
Refer to the examples to see different use cases of setting and overriding options.
💡 Missing a Stack / Option / Integration ?
Is your favorite self-hosted app not included yet? Or would you like to see additional options or integrations? I'm always looking to expand the collection! Feel free to open an issue or contribute directly with a pull request.
Settings Options
Most stacks will rely on some central settings. An example would be the base location where containers should create bind mounts for persistent data.
The following list contains all of the central settings.
nps.enableSocket
Whether to enable the Podman socket for user services. Note that the socket is required for the services like Traefik or Homepage to run successfully, since they access the Podman API.
If this is disabled and you use these services, you will need to manually enable the socket.
Type: boolean
Default:
true
Declared by:
nps.package
The podman package to use.
Type: package
Default:
pkgs.podman
Declared by:
nps.defaultGid
GID of the user that will be used by default for containers if they allow GID configuration. When running rootless containers, GID 0 gets mapped to the host users GID.
Type: signed integer
Default:
0
Declared by:
nps.defaultTz
Default timezone for containers.
Will be passed to all containers as TZ environment variable.
Type: null or string
Default:
"Etc/UTC"
Declared by:
nps.defaultUid
UID of the user that will be used by default for containers if they allow UID configuration. When running rootless containers, UID 0 gets mapped to the host users UID.
Type: signed integer
Default:
0
Declared by:
nps.externalStorageBaseDir
Base location that will be used for larger data such as downloads or media files. Could be an external disk.
Type: absolute path
Declared by:
nps.hostIP4Address
The IPv4 address which will be used in case explicit bindings are required.
Type: string
Declared by:
nps.hostUid
UID of the host user running the containers. Will be used to infer the Podman socket location (XDG_RUNTIME_DIR).
Type: signed integer
Default:
1000
Declared by:
nps.mediaStorageBaseDir
Base location for larger media files. This is where containers like Jellyfin or Immich will store their media files.
Type: absolute path
Default:
"${config.nps.externalStorageBaseDir}/media"
Declared by:
nps.socketLocation
The location of the Podman socket for user services. Will be passed to containers that communicate with the Podman API, such as Traefik, Homepage or Beszel.
Type: absolute path (read only)
Default:
"/run/user/${toString config.nps.hostUid}/podman/podman.sock"
Declared by:
nps.storageBaseDir
Base directory for Podman storage.
This is where each stack will create its bind mounts for persistent data.
For example, setting this to /home/foo/stacks would result in Adguard creating its bind mount at /home/foo/stacks/adguard.
Type: absolute path
Default:
"${config.home.homeDirectory}/stacks"
Declared by:
Container Options
This project extends Home Managers existing services.podman.containers options, to provide additional abstractions for example for Traefik or Homepage.
The options can be set directly on services.podman.container level, or through the stack aliases provided with this project.
For example, the following two configurations are equivalent:
nps.stacks = {
streaming.containers.jellyfin.expose = true;
};
services.podman.containers.jellyfin.expose = true;
The following lists all extension options that will be added by this project.
services.podman.containers.<name>.alloy.enable
Whether to enable Alloy Log Scraping. If enabled, Alloy will scrape logs from the container and ship them to Loki.; .
Type: boolean
Default:
false
Example:
true
Declared by:
services.podman.containers.<name>.dependsOn
List of systemd resources that this container depends on.
This is a hard requirement and will setup systemd Require and After attributes.
When specifying a dependency on another container, use the option dependsOnContainer instead.
See
- https://www.freedesktop.org/software/systemd/man/latest/systemd.unit.html#Requires=
- https://www.freedesktop.org/software/systemd/man/latest/systemd.unit.html#Before=
Type: list of string
Default:
[ ]
Declared by:
services.podman.containers.<name>.dependsOnContainer
List of containers that this container depends on.
Similar to dependsOn, but will automatically apply correct pre- and suffix for
the generated systemd services.
Type: list of string
Default:
[ ]
Declared by:
services.podman.containers.<name>.environment
This option has no description.
Type: unspecified value
Declared by:
services.podman.containers.<name>.expose
Whether the service should be exposed (e.g. reachable from external IP addresses).
When set to false, the private middleware will be applied by Traefik. The private middleware will only allow requests from
private CIDR ranges.
When set to true, the public middleware will be applied. The public middleware will allow access from the internet. It will be configured
with a rate limit, security headers and a geoblock plugin (if enabled). If enabled, Crowdsec will also
be added to the public middleware chain.
Type: boolean
Default:
false
Declared by:
services.podman.containers.<name>.extraEnv
Convinience wrapper option for passing environment variables to the container. The values of the environment variables can either be a primitive value or a path to a file.
In case of passing a path (using the fromFile attribure), the file will be read and the content will be set as the value of the environment variable.
Useful for containers that don’t support passing environment variables using the “_FILE” pattern.
Type: attribute set of (null or boolean or signed integer or string or absolute path or (submodule))
Default:
{ }
Example:
{
API_KEY = {
fromFile = "/home/user/api-key";
};
DB_PASSWORD = {
fromFile = "/some/path/secrets/db-password";
};
DB_URL = {
fromTemplate = "postgresql://user:{{ file.Read `/run/secrets/db_password` }}@localhost:5432/mydb";
};
ENCRYPTION_KEY = "literal-value";
}
Declared by:
services.podman.containers.<name>.fileEnvMount
Convenience wrapper option, that simplifies passing _FILE based environment variables.
For each attribute in the attrset, a volume mapping from sourcePath to destPath will be added,
and an environment variable will be set to the destPath.
Example:
API_KEY_FILE = {
srcPath = "/host/api-key.txt";
dstPath = "/container/api-key.txt";
};
will add a volume to the container, e.g.:
volumes = [${sourcePath}:${destPath}];
and also add an environment variable:
env.API_KEY_FILE = destPath;
You can also provide a simple path, which will be treated as the sourcePath:
DB_PASSWORD_FILE = ./secrets/db-password.txt;
The destPath will be inferred.
Type: attribute set of (absolute path or (submodule))
Default:
{ }
Example:
{
API_KEY_FILE = {
destPath = "/app/config/api-key.txt";
sourcePath = "/secrets/api-key.txt";
};
DB_PASSWORD_FILE = "/run/secrets/db-password.txt";
}
Declared by:
services.podman.containers.<name>.forwardAuth.enable
Whether to enable forward auth. This will enable the authelia Traefik middleware for this container.
Every request will be forwarded to be authorized by Authelia first.
Optionally, access control rules for this container can be specified in the settings. They will be added to the Authelia settings.
See https://www.authelia.com/configuration/security/access-control/
Type: boolean
Default:
false
Declared by:
services.podman.containers.<name>.forwardAuth.middlewareOrder
Order of the authelia middleware. Multiple middlewares will be called in order by Traefik, with lower orders
being called first.
Type: signed integer
Default:
1000
Declared by:
services.podman.containers.<name>.forwardAuth.rules
Rules matching a request. When all criteria of a rule match the request, the defined policy is applied.
See https://www.authelia.com/configuration/security/access-control/#rules
Type: list of (submodule)
Default:
[ ]
Declared by:
services.podman.containers.<name>.forwardAuth.rules.*.domain
Domain(s) that will be matched for the rule. Defaults to the servie domain registered in Traefik.
Either this, or the domain_regex options has to be set.
See https://www.authelia.com/configuration/security/access-control/#domain
Type: list of string
Default:
[ containerCfg.traefik.serviceHost ]
Declared by:
services.podman.containers.<name>.forwardAuth.rules.*.domain_regex
Regex(es) criteria matching the domain. Defaults to the servie domain registered in Traefik. Has to be set if the domain is unset.
See https://www.authelia.com/configuration/security/access-control/#domain_regex
Type: list of string
Default:
[ ]
Declared by:
services.podman.containers.<name>.forwardAuth.rules.*.methods
Critera matching the HTTP request method.
See https://www.authelia.com/configuration/security/access-control/#methods
Type: list of string
Default:
[ ]
Declared by:
services.podman.containers.<name>.forwardAuth.rules.*.networks
Critera matching the network. Can be a list of IP addresses, CIDR ranges or named network definitions.
See https://www.authelia.com/configuration/security/access-control/#networks
Type: list of string
Default:
[ ]
Declared by:
services.podman.containers.<name>.forwardAuth.rules.*.policy
The specific policy to apply to the selected rule. This is not criteria for a match, this is the action to take when a match is made.
See https://www.authelia.com/configuration/security/access-control/#policy
Type: one of “”, “deny”, “bypass”, “one_factor”, “two_factor”
Default:
""
Declared by:
services.podman.containers.<name>.forwardAuth.rules.*.resources
Critera matching the path and query parameter using regular expressions.
See https://www.authelia.com/configuration/security/access-control/#resources
Type: list of string
Default:
[ ]
Declared by:
services.podman.containers.<name>.forwardAuth.rules.*.subject
Criteria that matches the subject.
See https://www.authelia.com/configuration/security/access-control/#subject
Type: list of (string or list of string)
Default:
[ ]
Declared by:
services.podman.containers.<name>.forwardAuth.rulesOrder
Order of rules when merged into the authelia settings.
The order will be applied using lib.mkOrder <order> when applying the rules in the Authelia settings.
Lower numbers mean the rules will appear earlier in the access_control.rules list, which give them a higher priority.
Type: signed integer
Default:
1000
Declared by:
services.podman.containers.<name>.gatus.enable
Whether to enable gatus.
Type: boolean
Default:
false
Example:
true
Declared by:
services.podman.containers.<name>.gatus.settings
Endpoint Settings for the container. Will be added to the Gatus endpoint configuration.
See https://github.com/TwiN/gatus?tab=readme-ov-file#endpoints
Type: YAML 1.1 value
Default:
{ }
Declared by:
services.podman.containers.<name>.glance
Settings for the service.
See https://github.com/glanceapp/glance/blob/main/docs/configuration.md#docker-containers
Type: YAML 1.1 value
Default:
{ }
Declared by:
services.podman.containers.<name>.glance.category
The category under which the service will be listed on the dashboard.
Type: null or string
Default:
null
Declared by:
services.podman.containers.<name>.glance.name
The name of the service as it will displayed on the dashboard.
Type: string
Default:
lib.toSentenceCase <containerName>
Declared by:
services.podman.containers.<name>.glance.url
The URL of the service.
Type: string
Default:
""
Declared by:
services.podman.containers.<name>.homepage.category
The category under which the service will be listed on the Homepage dashboard.
Type: null or string
Default:
null
Declared by:
services.podman.containers.<name>.homepage.name
The name of the service as it will appear on the Homepage dashboard. Defaults to the container name.
Type: string
Default:
lib.toSentenceCase <containerName>
Declared by:
services.podman.containers.<name>.homepage.settings
Settings for the Homepage service. This can include icon, href, description, widget configuration, etc.
See https://gethomepage.dev/configs/services/#services/
Type: YAML 1.1 value
Default:
{ }
Declared by:
services.podman.containers.<name>.port
Main port that Traefik will forward traffic to. If Traefik is disabled, it will instead be added to the “ports” section
Type: null or string or signed integer
Default:
null
Declared by:
services.podman.containers.<name>.socketActivation
List of socket activation configurations for this container. Each entry should specify a port and optionally a file descriptor name. This will create a systemd socket that activates the container when accessed.
Will be used by containers like Traefik by default. Allows the container to access real-ip without the request being proxied through pasta/slirp4netns.
For details regarding rootless Podman networking and socket activation, see: https://github.com/eriksjolund/podman-networking-docs
Type: list of (submodule)
Default:
[ ]
Declared by:
services.podman.containers.<name>.socketActivation.*.fileDescriptorName
Name of the file descriptor that the socket should use.
Type: null or string
Default:
null
Declared by:
services.podman.containers.<name>.socketActivation.*.port
Port that the socket should listen on
Type: string or 16 bit unsigned integer; between 0 and 65535 (both inclusive)
Declared by:
services.podman.containers.<name>.stack
Stack that a container is part of. For every stack, a Podman networking will be crearted that the respective container will be connected to.
Type: null or string
Default:
null
Declared by:
services.podman.containers.<name>.templateMount
Bind mount that will render the template with gomplate.
The resulting file will be mounted into the container.
All environment variables from the environment and extraEnv options will be available for
substitution.
See
Type: list of (submodule)
Default:
[ ]
Example:
[
{
templatePath = pkgs.writeText "some-template" ''
Hello {{ env.GetEnv "USER" "you" }}
Secret Password is: {{ file.ReadFile "/run/secrets/some_secret" }}
'';
destPath = "/run/secrets/templated_file";
}
]
Declared by:
services.podman.containers.<name>.templateMount.*.destPath
Destination path of the templated file within the container
Type: absolute path
Declared by:
services.podman.containers.<name>.templateMount.*.templatePath
Path to the template. The file will be templated with gomplate before being mounted.
Type: absolute path
Declared by:
services.podman.containers.<name>.traefik.middleware
A mapping of middleware name to a boolean that indicated if the middleware should be applied to the service.
Type: attribute set of (submodule)
Default:
{ }
Declared by:
services.podman.containers.<name>.traefik.middleware.<name>.enable
Whether the middleware should be applied to the service
Type: boolean
Default:
false
Declared by:
services.podman.containers.<name>.traefik.middleware.<name>.order
Order of the middleware. Middlewares will be called in order by Traefik. Lower number means higher priority.
Type: signed integer
Default:
1000
Declared by:
services.podman.containers.<name>.traefik.name
The name of the service as it will be registered in Traefik. Will be used as a default for the subdomain.
If not set (null), the service will not be registered in Traefik.
Type: null or string
Default:
null
Declared by:
services.podman.containers.<name>.traefik.serviceAddressInternal
The internal main address of the service. Can be used for internal communication without going through Traefik, when inside the same Podman network.
Type: string (read only)
Default:
"${containerName}${containerCfg.port}"
Declared by:
services.podman.containers.<name>.traefik.serviceHost
The host name of the service as it will be registered in Traefik.
Type: string (read only)
Default:
"${traefikCfg.subDomain}.${nps.stacks.traefik.domain}"
Declared by:
services.podman.containers.<name>.traefik.serviceUrl
The full URL of the service as it will be registered in Traefik. This will be the serviceHost including the “https://” prefix.
Type: string (read only)
Default:
"https://${traefikCfg.serviceHost}"
Declared by:
services.podman.containers.<name>.traefik.subDomain
The subdomain of the service as it will be registered in Traefik.
Type: string
Default:
"traefikCfg.name"
Declared by:
services.podman.containers.<name>.wants
List of systemd resources that this container depends on.
Compared to dependsOn, this is a softer requirement and will setup systemd Wants and After attributes.
When specifying a dependency on another container, use the option wantsContainer instead.
See
- https://www.freedesktop.org/software/systemd/man/latest/systemd.unit.html#Wants=
- https://www.freedesktop.org/software/systemd/man/latest/systemd.unit.html#Before=
Type: list of string
Default:
[ ]
Declared by:
services.podman.containers.<name>.wantsContainer
List of containers that this container depends on.
Similar to dependsOn, but will automatically apply correct pre- and suffix for
the generated systemd services.
Type: list of string
Default:
[ ]
Declared by:
Stack Options
The nps.stacks options allow enabling and configuring various stacks.
Most stacks just require the enable option set to true. Some stacks can optionally be configured to adjust settings or pass environment files (e.g. for secrets).
If you want to make changes that are not possible through the exposed stack options directly, aliases to the services.podman.container options are provided, which let you override or modify any attribute that the stack modules set.
For instance, accessing nps.stacks.streaming.containers.jellyfin is an alias to services.podman.containers.jellyfin and allows editing any of the known services.podman.containers options, such as networks, volumes and environment files. Usually this should not be necessary though.
The following sub-pages contain the options for each available stack.
nps.stacks.adguard.enable
Whether to enable adguard.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.adguard.containers.adguard
Alias of services.podman.containers.adguard.
Type: submodule
Declared by:
nps.stacks.aiostreams.enable
Whether to enable aiostreams.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.aiostreams.containers.aiostreams
Alias of services.podman.containers.aiostreams.
Type: submodule
Declared by:
nps.stacks.aiostreams.extraEnv
Extra environment variables to set for the container.
Can be used to pass secrets such as the TMDB_ACCESS_TOKEN.
See https://github.com/Viren070/AIOStreams/wiki/Configuration
Type: attribute set of (null or boolean or signed integer or string or absolute path or (submodule))
Default:
{ }
Example:
{
FOO = "bar";
TMDB_ACCESS_TOKEN = {
fromFile = "/run/secrets/tmdb_access_token";
};
}
Declared by:
nps.stacks.audiobookshelf.enable
Whether to enable audiobookshelf.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.audiobookshelf.containers.audiobookshelf
Alias of services.podman.containers.audiobookshelf.
Type: submodule
Declared by:
nps.stacks.audiobookshelf.oidc.adminGroup
Users of this group will be assigned admin rights.
In order to take effect, you will have to enter the value abs_groups in the Group Claim form field in the Audiobookshelf UI.
Type: string
Default:
"audiobookshelf_admin"
Declared by:
nps.stacks.audiobookshelf.oidc.clientSecretHash
The hashed client_secret. For examples on how to generate a client secret, see
https://www.authelia.com/integration/openid-connect/frequently-asked-questions/#client-secret
Type: string
Declared by:
nps.stacks.audiobookshelf.oidc.registerClient
Whether to register a Audiobookshelf OIDC client in Authelia.
If enabled you need to provide a hashed secret in the client_secret option.
To enable OIDC Login for Audiobookshelf, you will have to enable it in the Web UI.
For details, see:
- https://www.authelia.com/integration/openid-connect/clients/audiobookshelf/
- https://www.audiobookshelf.org/guides/oidc_authentication/#configuring-audiobookshelf-for-sso
Type: boolean
Default:
false
Declared by:
nps.stacks.audiobookshelf.oidc.userGroup
Users of this group will be able to log in
In order to take effect, you will have to enter the value abs_groups in the Group Claim form field in the Audiobookshelf UI.
Type: string
Default:
"audiobookshelf_user"
Declared by:
nps.stacks.authelia.enable
Whether to enable authelia.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.authelia.enableTraefikMiddleware
Wheter to register an authelia middleware for Traefik.
The middleware will utilize the ForwardAuth Authz implementation.
See https://www.authelia.com/integration/proxies/traefik/#implementation
Type: boolean
Default:
config.nps.stacks.traefik.enable
Declared by:
nps.stacks.authelia.containers.authelia
Alias of services.podman.containers.authelia.
Type: submodule
Declared by:
nps.stacks.authelia.containers.authelia-redis
Alias of services.podman.containers.authelia-redis.
Type: submodule
Declared by:
nps.stacks.authelia.crowdsec.enableLogCollection
Whether the container logs should be collected by CrowdSec. Enabling this will configure the acquis settings for CrowdSec.
Type: boolean
Default:
config.nps.stacks.crowdsec.enable
Declared by:
nps.stacks.authelia.defaultAllowPolicy
Default policy to apply for allowed access. Will be used as a default for Access Control Rules as well as OIDC Authorization Policies if no rules apply.
See
- https://www.authelia.com/configuration/identity-providers/openid-connect/clients/#authorization_policy
- https://www.authelia.com/configuration/security/access-control/#rules
Type: one of “one_factor”, “two_factor”
Default:
"one_factor"
Declared by:
nps.stacks.authelia.jwtSecretFile
Path to the file containing the JWT secret. See https://www.authelia.com/configuration/identity-validation/reset-password/#jwt_secret
Type: absolute path
Declared by:
nps.stacks.authelia.ldap.passwordFile
The password for the LDAP user that is used when connecting to the LDAP backend.
Type: absolute path
Default:
config.nps.stacks.lldap.adminPasswordFile
Declared by:
nps.stacks.authelia.ldap.username
The username that will be used when binding to the LDAP backend.
Type: string
Default:
config.nps.stacks.lldap.adminUsername
Declared by:
nps.stacks.authelia.oidc.enable
Whether to enable OIDC Support.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.authelia.oidc.clients
OIDC client configuration. See https://www.authelia.com/configuration/identity-providers/openid-connect/clients/
Type: attribute set of (YAML 1.1 value)
Default:
{ }
Declared by:
nps.stacks.authelia.oidc.clients.<name>.client_id
This option has no description.
Type: string
Default:
"‹name›"
Declared by:
nps.stacks.authelia.oidc.defaultConsentDuration
Default period of how long a users choice to remember the pre-configured consent lasts.
Only has an effect for OIDC clients using the consent_mode pre-configured or auto.
See
Type: string
Default:
"1 month"
Declared by:
nps.stacks.authelia.oidc.hmacSecretFile
Path to the file containing the HMAC secret. See https://www.authelia.com/configuration/identity-providers/openid-connect/provider/#hmac_secret
Type: absolute path
Declared by:
nps.stacks.authelia.oidc.jwksRsaKeyFile
Path to the file containing the JWKS RSA (RS256) private key.
For example, a keypair can be generated and printed out like this:
podman run --rm authelia/authelia sh -c "authelia crypto certificate rsa generate --common-name authelia.example.com && cat public.crt && cat private.pem"
See https://www.authelia.com/configuration/identity-providers/openid-connect/provider/#key
Type: absolute path
Declared by:
nps.stacks.authelia.sessionProvider
‘’ Session provider to use.
See <https://www.authelia.com/configuration/session/introduction/>
''
Type: one of “memory”, “redis”
Default:
"memory"
Declared by:
nps.stacks.authelia.sessionSecretFile
Path to the file containing the session secret. See https://www.authelia.com/configuration/session/introduction/#secret
Type: absolute path
Declared by:
nps.stacks.authelia.settings
Additional Authelia settings. Will be provided in the configuration.yml.
Type: YAML 1.1 value
Declared by:
nps.stacks.authelia.storageEncryptionKeyFile
Path to the file containing the storage encryption key. See https://www.authelia.com/configuration/storage/introduction/#encryption_key
Type: absolute path
Declared by:
nps.stacks.baikal.enable
Whether to enable baikal.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.baikal.containers.baikal
Alias of services.podman.containers.baikal.
Type: submodule
Declared by:
nps.stacks.beszel.enable
Whether to enable beszel.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.beszel.containers.beszel
Alias of services.podman.containers.beszel.
Type: submodule
Declared by:
nps.stacks.beszel.containers.beszel-agent
Alias of services.podman.containers.beszel-agent.
Type: submodule
Declared by:
nps.stacks.beszel.ed25519PrivateKeyFile
Path to private SSH key that will be used by the hub to authenticate against agent If not provided, the hub will generate a new key pair when starting.
Type: null or absolute path
Default:
null
Declared by:
nps.stacks.beszel.ed25519PublicKeyFile
Path to public SSH key of the hub that will be considered authorized by agent
If not provided, the KEY environment variable should be set to the public key of the hub,
in order for the connection from hub to agent to work.
Type: null or absolute path
Default:
null
Declared by:
nps.stacks.beszel.oidc.clientSecretHash
The hashed client_secret. For examples on how to generate a client secret, see
https://www.authelia.com/integration/openid-connect/frequently-asked-questions/#client-secret
Type: string
Declared by:
nps.stacks.beszel.oidc.registerClient
Whether to register a Beszel OIDC client in Authelia.
If enabled you need to provide a hashed secret in the client_secret option.
To enable OIDC Login for Beszel, you will have to set it up in Beszels Web-UI. For details, see:
Type: boolean
Default:
false
Declared by:
nps.stacks.beszel.oidc.userGroup
Users of this group will be able to log in
Type: string
Default:
"beszel_user"
Declared by:
nps.stacks.beszel.settings
System configuration (optional). If provided, on each restart, systems in the database will be updated to match the systems defined in the settings. To see your current configuration, refer to settings -> YAML Config -> Export configuration
Type: null or YAML 1.1 value
Default:
null
Example:
{
systems = [
{
host = "/beszel_socket/beszel.sock";
name = "Local";
port = 45876;
users = [
"admin@example.com"
];
}
];
}
Declared by:
nps.stacks.beszel.useSocketProxy
Whether to access the Podman socket through the read-only proxy for the beszel stack. Will be enabled by default if the ‘docker-socket-proxy’ stack is enabled.
Type: boolean
Default:
config.nps.stacks.docker-socket-proxy.enable
Declared by:
nps.stacks.blocky.enable
Whether to enable blocky.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.blocky.enableGrafanaDashboard
Whether to enable Grafana Dashboard.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.blocky.enablePrometheusExport
Whether to enable Prometheus Export.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.blocky.containers.blocky
Alias of services.podman.containers.blocky.
Type: submodule
Declared by:
nps.stacks.blocky.settings
Blocky configuration. Will be converted to the config.yml.
For a full list of options, refer to the Blocky documentation
By default, if Traefik is enabled, the module will automatically setup a DNS override pointing the Traefik domain to your host IP.
Type: YAML 1.1 value
Declared by:
nps.stacks.booklore.enable
Whether to enable booklore.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.booklore.containers.booklore
Alias of services.podman.containers.booklore.
Type: submodule
Declared by:
nps.stacks.booklore.containers.booklore-db
Alias of services.podman.containers.booklore-db.
Type: submodule
Declared by:
nps.stacks.booklore.db.rootPasswordFile
Path to the file containing the password for the MariaDB root user
Type: absolute path
Declared by:
nps.stacks.booklore.db.userPasswordFile
Path to the file containing the password for the romm database user
Type: absolute path
Declared by:
nps.stacks.booklore.oidc.registerClient
Whether to register a Booklore OIDC client in Authelia. To enable OIDC Login for Booklore, you will have to enable it in the Web UI.
For details, see:
- https://www.authelia.com/integration/openid-connect/clients/booklore/
- https://booklore-app.github.io/booklore-docs/docs/authentication/authelia
Type: boolean
Default:
false
Declared by:
nps.stacks.booklore.oidc.userGroup
Users of this group will be able to log in
Type: string
Default:
"booklore_user"
Declared by:
nps.stacks.bytestash.enable
Whether to enable bytestash.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.bytestash.containers.bytestash
Alias of services.podman.containers.bytestash.
Type: submodule
Declared by:
nps.stacks.bytestash.extraEnv
Extra environment variables to set for the container. Variables can be either set directly or sourced from a file (e.g. for secrets).
See https://github.com/jordan-dalby/ByteStash/wiki/FAQ#environment-variables
Type: attribute set of (null or boolean or signed integer or string or absolute path or (submodule))
Default:
{ }
Example:
{
FOO = "bar";
SOME_SECRET = {
fromFile = "/run/secrets/secret_name";
};
}
Declared by:
nps.stacks.calibre.enable
Whether to enable calibre.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.calibre.containers.calibre
Alias of services.podman.containers.calibre.
Type: submodule
Declared by:
nps.stacks.calibre.containers.calibre-downloader
Alias of services.podman.containers.calibre-downloader.
Type: submodule
Declared by:
nps.stacks.changedetection.enable
Whether to enable changedetection.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.changedetection.containers.changedetection
Alias of services.podman.containers.changedetection.
Type: submodule
Declared by:
nps.stacks.changedetection.containers.sockpuppetbrowser
Alias of services.podman.containers.sockpuppetbrowser.
Type: submodule
Declared by:
nps.stacks.crowdsec.enable
Whether to enable crowdsec.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.crowdsec.enableGrafanaDashboard
Whether to enable Grafana Dashboard.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.crowdsec.enablePrometheusExport
Whether to enable Prometheus Export.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.crowdsec.acquisSettings
Acquisitions settings for Crowdsec.
Each attribute set value will be mapped to an acquis configuration and mounted into the /etc/crowdsec/acquis.d directory.
See https://docs.crowdsec.net/docs/next/log_processor/data_sources/intro for all available options.
Type: attribute set of (YAML 1.1 value)
Default:
{ }
Declared by:
nps.stacks.crowdsec.acquisSettings.<name>.labels
A map of labels to add to the event. The type label is mandatory, and used by the Security Engine to choose which parser to use.
See https://docs.crowdsec.net/docs/next/log_processor/data_sources/intro#labels
Type: YAML 1.1 value
Default:
{ }
Declared by:
nps.stacks.crowdsec.acquisSettings.<name>.labels.type
This option has no description.
Type: string
Declared by:
nps.stacks.crowdsec.acquisSettings.<name>.log_level
Log level to use in the datasource
Type: string
Default:
"info"
Declared by:
nps.stacks.crowdsec.acquisSettings.<name>.source
Which type of datasource to use.
Type: string
Example:
"docker"
Declared by:
nps.stacks.crowdsec.collections
Collections to install. Will be passed as the COLLECTIONS environment variable.
See https://app.crowdsec.net/hub/collections
Type: strings concatenated with " "
Default:
""
Example:
"LePresidente/adguardhome crowdsecurity/aws-console"
Declared by:
nps.stacks.crowdsec.containers.crowdsec
Alias of services.podman.containers.crowdsec.
Type: submodule
Declared by:
nps.stacks.crowdsec.extraEnv
Extra environment variables to set for the container. Variables can be either set directly or sourced from a file (e.g. for secrets).
See https://github.com/crowdsecurity/crowdsec/blob/master/docker/README.md#environment-variables
Type: attribute set of (null or boolean or signed integer or string or absolute path or (submodule))
Default:
{ }
Example:
{
FOO = "bar";
SOME_SECRET = {
fromFile = "/run/secrets/secret_name";
};
}
Declared by:
nps.stacks.crowdsec.settings
Configuration settings for Crowdsec.
Will be provided as the config.yaml.local file.
See https://docs.crowdsec.net/docs/configuration/crowdsec_configuration/
Type: YAML 1.1 value
Default:
{ }
Declared by:
nps.stacks.crowdsec.useSocketProxy
Whether to access the Podman socket through the read-only proxy for the crowdsec stack. Will be enabled by default if the ‘docker-socket-proxy’ stack is enabled.
Type: boolean
Default:
config.nps.stacks.docker-socket-proxy.enable
Declared by:
nps.stacks.davis.enable
Whether to enable davis.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.davis.enableLdapAuth
Whether to enable login via LLDAP as an auth provider
Type: boolean
Default:
config.nps.stacks.lldap.enable
Declared by:
nps.stacks.davis.adminPasswordFile
Path to the file containing the admin password.
Type: absolute path
Declared by:
nps.stacks.davis.adminUsername
Admin username to access the dashboard.
Type: string
Default:
"admin"
Declared by:
nps.stacks.davis.containers.davis
Alias of services.podman.containers.davis.
Type: submodule
Declared by:
nps.stacks.davis.db.rootPasswordFile
Path to the file containing the password for the MySQL root user.
Type: absolute path
Declared by:
nps.stacks.davis.db.type
Type of the database to use.
Can be set to “sqlite” or “mysql”.
If set to “mysql”, the userPasswordFile and rootPasswordFile options must be set.
Type: one of “sqlite”, “mysql”
Default:
"mysql"
Declared by:
nps.stacks.davis.db.userPasswordFile
Path to the file containing the password for the davis database user.
Type: absolute path
Declared by:
nps.stacks.davis.db.username
Username for the davis database user.
Type: string
Default:
"davis"
Declared by:
nps.stacks.davis.extraEnv
Extra environment variables to set for the container. Variables can be either set directly or sourced from a file (e.g. for secrets).
See https://github.com/tchapi/davis/blob/main/docker/.env
Type: attribute set of (null or boolean or signed integer or string or absolute path or (submodule))
Default:
{ }
Example:
{
MAIL_HOST = "smtp.myprovider.com";
MAIL_PASSWORD = {
fromFile = "/run/secrets/secret_name";
};
}
Declared by:
nps.stacks.dockdns.enable
Whether to enable DockDNS. This will run a Cloudflare DNS client that updates DNS records based on Docker labels.
The module contains an extension that will automatically create DNS records for services with the public Traefik middleware,
so they are accessible from the internet. Optionally it will also automatically delete DNS records for services, that are no longer exposed (e.g. private middleware)
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.dockdns.containers.dockdns
Alias of services.podman.containers.dockdns.
Type: submodule
Declared by:
nps.stacks.dockdns.extraEnv
Extra environment variables to set for the container. Variables can be either set directly or sourced from a file (e.g. for secrets).
See https://github.com/crowdsecurity/crowdsec/blob/master/docker/README.md#environment-variables
Type: attribute set of (null or boolean or signed integer or string or absolute path or (submodule))
Default:
{ }
Example:
{
FOO = "bar";
SOME_SECRET = {
fromFile = "/run/secrets/secret_name";
};
}
Declared by:
nps.stacks.dockdns.settings
Settings for DockDNS.
For details, refer to the DockDNS documentation
The module will provide a default configuration, that updates DNS records every 10 minutes.
DockDNS labels will be automatically added to services with the public Traefik middleware.
Type: YAML 1.1 value
Declared by:
nps.stacks.dockdns.useSocketProxy
Whether to access the Podman socket through the read-only proxy for the dockdns stack. Will be enabled by default if the ‘docker-socket-proxy’ stack is enabled.
Type: boolean
Default:
config.nps.stacks.docker-socket-proxy.enable
Declared by:
nps.stacks.docker-socket-proxy.enable
Whether to enable docker-socket-proxy.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.docker-socket-proxy.containers.docker-socket-proxy
Alias of services.podman.containers.docker-socket-proxy.
Type: submodule
Declared by:
nps.stacks.donetick.enable
Whether to enable donetick.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.donetick.containers.donetick
Alias of services.podman.containers.donetick.
Type: submodule
Declared by:
nps.stacks.donetick.jwtSecretFile
Path to the file containing the JWT secret.
Type: absolute path
Declared by:
nps.stacks.donetick.oidc.enable
Whether to enable OIDC login with Authelia. This will register an OIDC client in Authelia and setup the necessary configuration.
For details, see:
- https://www.authelia.com/integration/openid-connect/clients/donetick/
- https://docs.donetick.com/advance-settings/openid-connect-setup/
Type: boolean
Default:
false
Declared by:
nps.stacks.donetick.oidc.clientSecretFile
The file containing the client secret for the OIDC client that will be registered in Authelia.
Type: string
Declared by:
nps.stacks.donetick.oidc.clientSecretHash
The hashed client_secret. Will be set in the Authelia client config. For examples on how to generate a client secret, see
https://www.authelia.com/integration/openid-connect/frequently-asked-questions/#client-secret
Type: string
Declared by:
nps.stacks.donetick.oidc.userGroup
Users of this group will be able to log in
Type: string
Default:
"donetick_user"
Declared by:
nps.stacks.donetick.settings
Additional donetick settings. Will be provided as the selhosted.yaml file.
See https://github.com/donetick/donetick/blob/main/config/selfhosted.yaml
Type: YAML 1.1 value
Default:
{ }
Declared by:
nps.stacks.dozzle.enable
Whether to enable Dozzle.
The module contains an extension that will automatically add all containers to Dozzle groups,
if they stack attribute is set.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.dozzle.containers.dozzle
Alias of services.podman.containers.dozzle.
Type: submodule
Declared by:
nps.stacks.dozzle.useSocketProxy
Whether to access the Podman socket through the read-only proxy for the dozzle stack. Will be enabled by default if the ‘docker-socket-proxy’ stack is enabled.
Type: boolean
Default:
config.nps.stacks.docker-socket-proxy.enable
Declared by:
nps.stacks.filebrowser.enable
Whether to enable filebrowser.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.filebrowser.containers.filebrowser
Alias of services.podman.containers.filebrowser.
Type: submodule
Declared by:
nps.stacks.filebrowser.mounts
Mount points for the file browser.
Format: { 'hostPath' = 'containerPath' }
By default, the users home directory and the external storage directory (config.nps.externalStorageBaseDir)
are configured as mounts.
Type: attribute set of string
Example:
{
"/home/foo/media" = "/media";
"/mnt/ext/data" = "/data";
}
Declared by:
nps.stacks.filebrowser-quantum.enable
Whether to enable filebrowser-quantum.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.filebrowser-quantum.containers.filebrowser-quantum
Alias of services.podman.containers.filebrowser-quantum.
Type: submodule
Declared by:
nps.stacks.filebrowser-quantum.mounts
Mount configuration for the file browser.
Format: { 'hostPath' = container-source-config }
The mounts will be added to the settings source section and a volume mount will be added for each configured source.
Type: attribute set of (submodule)
Default:
{ }
Example:
{
"/home/foo/media" = {
config = {
disableIndexing = false;
exclude = {
fileEndsWith = [
".zip"
".txt"
];
};
};
path = "/media";
};
"/mnt/ext/data" = {
name = "ext-data";
path = "/data";
};
}
Declared by:
nps.stacks.filebrowser-quantum.mounts.<name>.config
Additional configuration options for the source.
Type: YAML 1.1 value
Default:
{ }
Declared by:
nps.stacks.filebrowser-quantum.mounts.<name>.name
Optional name of the source, otherwise the source gets named the folder name
Type: null or string
Default:
null
Example:
"folder"
Declared by:
nps.stacks.filebrowser-quantum.mounts.<name>.path
Path of the source in the container
Type: absolute path
Example:
"/mnt/folder"
Declared by:
nps.stacks.filebrowser-quantum.oidc.enable
Whether to enable OIDC login with Authelia. This will register an OIDC client in Authelia and setup the necessary configuration.
For details, see:
- https://www.authelia.com/integration/openid-connect/clients/filebrowser-quantum/
- https://github.com/gtsteffaniak/filebrowser/wiki/Configuration-And-Examples#openid-connect-configuration-oidc
Type: boolean
Default:
false
Declared by:
nps.stacks.filebrowser-quantum.oidc.adminGroup
Users of this group will be assigned admin rights
Type: string
Default:
"filebrowser-quantum_admin"
Declared by:
nps.stacks.filebrowser-quantum.oidc.clientSecretFile
The file containing the client secret for the OIDC client that will be registered in Authelia.
Type: string
Declared by:
nps.stacks.filebrowser-quantum.oidc.clientSecretHash
The hashed client_secret. Will be set in the Authelia client config. For examples on how to generate a client secret, see
https://www.authelia.com/integration/openid-connect/frequently-asked-questions/#client-secret
Type: string
Declared by:
nps.stacks.filebrowser-quantum.oidc.userGroup
Users of this group will be able to log in
Type: string
Default:
"filebrowser-quantum_user"
Declared by:
nps.stacks.filebrowser-quantum.settings
Settings that will be added to the config.yml.
To configure sources, you should prefer using the mounts option, as the corresponding volume mappings will be
configured automatically.
Type: YAML 1.1 value
Declared by:
nps.stacks.forgejo.enable
Whether to enable forgejo.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.forgejo.containers.forgejo
Alias of services.podman.containers.forgejo.
Type: submodule
Declared by:
nps.stacks.forgejo.settings
Optional app settings for Forgejo. For a full list of options, refer to the Forgejo documentation.
Type: null or (attribute set of section of an INI file (attrs of INI atom (null, bool, int, float or string)))
Default:
null
Declared by:
nps.stacks.freshrss.enable
Whether to enable freshrss.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.freshrss.adminProvisioning.enable
Whether to automatically create an admin user on the first run. If set to false, you will be prompted to create an admin user when visiting the FreshRSS web interface for the first time. This only affects the first run of the container.
If you want to use OIDC login, disable this option. The first logged in OIDC user will be admin in that case. See https://freshrss.github.io/FreshRSS/en/admins/16_OpenID-Connect.html
Type: boolean
Default:
false
Declared by:
nps.stacks.freshrss.adminProvisioning.apiPasswordFile
Path to a file containing the admin API password
Type: absolute path
Default:
null
Declared by:
nps.stacks.freshrss.adminProvisioning.email
Email address for the admin user
Type: string
Declared by:
nps.stacks.freshrss.adminProvisioning.passwordFile
Path to a file containing the admin user password
Type: absolute path
Default:
null
Declared by:
nps.stacks.freshrss.adminProvisioning.username
Username for the admin user
Type: string
Default:
"admin"
Declared by:
nps.stacks.freshrss.containers.freshrss
Alias of services.podman.containers.freshrss.
Type: submodule
Declared by:
nps.stacks.freshrss.oidc.enable
Whether to enable OIDC login with Authelia. This will register an OIDC client in Authelia and setup the necessary configuration.
The first user created with OIDC login on initial setup will be admin. Make sure to follow the ‘Initial Setup Process’ instructions at https://freshrss.github.io/FreshRSS/en/admins/16_OpenID-Connect.html
For details, see:
- https://www.authelia.com/integration/openid-connect/clients/freshrss/
- https://freshrss.github.io/FreshRSS/en/admins/16_OpenID-Connect.html
Type: boolean
Default:
false
Declared by:
nps.stacks.freshrss.oidc.clientSecretFile
The file containing the client secret for the OIDC client that will be registered in Authelia.
Type: string
Declared by:
nps.stacks.freshrss.oidc.clientSecretHash
The hashed client_secret. Will be set in the Authelia client config. For examples on how to generate a client secret, see
https://www.authelia.com/integration/openid-connect/frequently-asked-questions/#client-secret
Type: string
Declared by:
nps.stacks.freshrss.oidc.cryptoKeyFile
Opaque key used for internal encryption.
Type: string
Declared by:
nps.stacks.freshrss.oidc.userGroup
Users of this group will be able to log in
Type: string
Default:
"freshrss_user"
Declared by:
nps.stacks.gatus.enable
Whether to enable Gatus. The module also provides an extension that will add Gatus options to a container. This allows services to be added to Gatus by settings container options.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.gatus.containers.gatus
Alias of services.podman.containers.gatus.
Type: submodule
Declared by:
nps.stacks.gatus.containers.gatus-db
Alias of services.podman.containers.gatus-db.
Type: submodule
Declared by:
nps.stacks.gatus.db.passwordFile
The file containing the PostgreSQL password for the database. Only used if db.type is set to “postgres”.
Type: absolute path
Declared by:
nps.stacks.gatus.db.type
Type of the database to use.
Can be set to “sqlite” or “postgres”.
If set to “postgres”, the passwordFile option must be set.
Type: one of “sqlite”, “postgres”
Default:
"sqlite"
Declared by:
nps.stacks.gatus.db.username
The PostgreSQL user to use for the database. Only used if db.type is set to “postgres”.
Type: string
Default:
"gatus"
Declared by:
nps.stacks.gatus.defaultEndpoint
Default endpoint settings. Will merged with each provided endpoint. Only applies if endpoint does not override the default endpoint settings.
Type: YAML 1.1 value
Default:
{
client = {
insecure = true;
timeout = "10s";
};
conditions = [
"[STATUS] >= 200"
"[STATUS] < 300"
];
group = "core";
interval = "5m";
}
Declared by:
nps.stacks.gatus.extraEnv
Extra environment variables to set for the container. Variables can be either set directly or sourced from a file (e.g. for secrets).
See https://github.com/TwiN/gatus?tab=readme-ov-file#configuration
Type: attribute set of (null or boolean or signed integer or string or absolute path or (submodule))
Default:
{ }
Example:
{
FOO = "bar";
SOME_SECRET = {
fromFile = "/run/secrets/secret_name";
};
}
Declared by:
nps.stacks.gatus.extraSettingsFiles
List of additional YAML files to include in the settings. These files will be mounted as is. Can be used to directly provide YAML files containing secrets, e.g. from sops
Type: list of absolute path
Default:
[ ]
Declared by:
nps.stacks.gatus.oidc.enable
Whether to enable OIDC login with Authelia. This will register an OIDC client in Authelia and setup the necessary configuration.
For details, see:
- https://www.authelia.com/integration/openid-connect/clients/gatus/
- https://github.com/TwiN/gatus?tab=readme-ov-file#oidc
Type: boolean
Default:
false
Declared by:
nps.stacks.gatus.oidc.clientSecretFile
The file containing the client secret for the Gatus OIDC client that will be registered in Authelia.
Type: string
Declared by:
nps.stacks.gatus.oidc.clientSecretHash
The hashed client_secret. Will be set in the Authelia client config. For examples on how to generate a client secret, see
https://www.authelia.com/integration/openid-connect/frequently-asked-questions/#client-secret
Type: string
Declared by:
nps.stacks.gatus.oidc.userGroup
Users of this group will be able to log in
Type: string
Default:
"gatus_user"
Declared by:
nps.stacks.gatus.settings
Settings for the Gatus container. Will be converted to YAML and passed to the container.
See https://github.com/TwiN/gatus
Type: YAML 1.1 value
Declared by:
nps.stacks.glance.enable
Whether to enable glance.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.glance.containers.glance
Alias of services.podman.containers.glance.
Type: submodule
Declared by:
nps.stacks.glance.settings
Settings that will be provided as the glance.yml configuration file.
See https://github.com/glanceapp/glance/blob/main/docs/configuration.md#configuring-glance
Type: YAML 1.1 value
Default:
{ }
Declared by:
nps.stacks.glance.settings.pages
This option has no description.
Type: attribute set of (YAML 1.1 value)
Declared by:
nps.stacks.glance.settings.pages.<name>.columns
The columns to display on the page
Type: attribute set of (YAML 1.1 value)
Declared by:
nps.stacks.glance.settings.pages.<name>.columns.<name>.rank
The order of the column on the page.
Type: signed integer
Default:
1000
Declared by:
nps.stacks.glance.settings.pages.<name>.columns.<name>.size
The size of the column.
Type: one of “small”, “full”
Declared by:
nps.stacks.glance.settings.pages.<name>.name
The name of the page. Default to the attribute name.
Type: string
Default:
lib.toSentenceCase <pageName>
Declared by:
nps.stacks.glance.useSocketProxy
Whether to access the Podman socket through the read-only proxy for the glance stack. Will be enabled by default if the ‘docker-socket-proxy’ stack is enabled.
Type: boolean
Default:
config.nps.stacks.docker-socket-proxy.enable
Declared by:
nps.stacks.glance.userCss
Custom CSS settings.
See https://github.com/glanceapp/glance/blob/main/docs/configuration.md#custom-css-file
Type: strings concatenated with “\n”
Default:
""
Declared by:
nps.stacks.guacamole.enable
Whether to enable guacamole.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.guacamole.containers.guacamole
Alias of services.podman.containers.guacamole.
Type: submodule
Declared by:
nps.stacks.guacamole.containers.guacamole-db
Alias of services.podman.containers.guacamole-db.
Type: submodule
Declared by:
nps.stacks.guacamole.db.enable
Whether to use a DB for authentication. This is required when OIDC is enabled.
See https://guacamole.apache.org/doc/gug/jdbc-auth.html#database-authentication
Type: boolean
Default:
false
Declared by:
nps.stacks.guacamole.db.passwordFile
The file containing the PostgreSQL password for the database.
Type: absolute path
Declared by:
nps.stacks.guacamole.db.username
The PostgreSQL user to use for the database.
Type: string
Default:
"guacamole"
Declared by:
nps.stacks.guacamole.oidc.enable
Whether to enable OIDC login with Authelia. This will register an OIDC client in Authelia and setup the necessary configuration.
When OIDC is enabled, the db.passwordFile option has to be provided, as a DB setup is required for OIDC to work.
Users from the user-mapping.xml won’t be matched when logging in via OIDC.
For details, see:
- https://www.authelia.com/integration/openid-connect/clients/apache-guacamole/
- https://guacamole.apache.org/doc/gug/openid-auth.html
Type: boolean
Default:
false
Declared by:
nps.stacks.guacamole.userMappingXml
Path to file that is provided as the user-mapping.xml.
See https://guacamole.apache.org/doc/gug/configuring-guacamole.html#user-mapping-xml
Type: null or absolute path
Default:
null
Declared by:
nps.stacks.healthchecks.enable
Whether to enable healthchecks.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.healthchecks.containers.healthchecks
Alias of services.podman.containers.healthchecks.
Type: submodule
Declared by:
nps.stacks.healthchecks.secretKeyFile
Path to the file containing the secret key.
See https://healthchecks.io/docs/self_hosted_configuration/#SECRET_KEY
Type: absolute path
Declared by:
nps.stacks.healthchecks.superUserEmail
Email address of the superuser account
Type: string
Declared by:
nps.stacks.healthchecks.superUserPasswordFile
Path to the file containing the superuser password
Type: absolute path
Declared by:
nps.stacks.homeassistant.enable
Whether to enable homeassistant.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.homeassistant.containers.homeassistant
Alias of services.podman.containers.homeassistant.
Type: submodule
Declared by:
nps.stacks.homeassistant.settings
Settings that will be written to the ‘configuration.yaml’ file.
If you want to configure settings through the UI, set this option to null.
In that case, no managed configuration.yaml will be provided.
Type: null or YAML 1.1 value
Declared by:
nps.stacks.homepage.enable
Whether to enable the Homepage stack.
The services of enabled stacks will be automatically added to Homepage. The module will also automatically configure the docker integration for the local host and setup some widgets.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.homepage.bookmarks
Homepage bookmarks configuration.
See https://gethomepage.dev/configs/bookmarks/.
Type: YAML 1.1 value
Default:
[ ]
Example:
[
{
Developer = [
{
Github = [
{
abbr = "GH";
href = "https://github.com/";
}
];
}
];
}
{
Entertainment = [
{
YouTube = [
{
abbr = "YT";
href = "https://youtube.com/";
}
];
}
];
}
]
Declared by:
nps.stacks.homepage.containers.homepage
Alias of services.podman.containers.homepage.
Type: submodule
Declared by:
nps.stacks.homepage.docker
Homepage docker configuration.
See https://gethomepage.dev/configs/docker/.
Type: YAML 1.1 value
Default:
{ }
Declared by:
nps.stacks.homepage.services
Homepage services configuration.
See https://gethomepage.dev/configs/services/.
Type: YAML 1.1 value
Default:
{ }
Example:
{
"My First Group" = {
"My First Service" = {
description = "Some Service";
href = "http://localhost/";
};
};
"My Second Group" = {
"My Second Service" = {
description = "Some other Service";
href = "http://localhost/";
};
};
}
Declared by:
nps.stacks.homepage.settings
Homepage settings.
See https://gethomepage.dev/configs/settings/.
Type: YAML 1.1 value
Default:
{ }
Declared by:
nps.stacks.homepage.useSocketProxy
Whether to access the Podman socket through the read-only proxy for the homepage stack. Will be enabled by default if the ‘docker-socket-proxy’ stack is enabled.
Type: boolean
Default:
config.nps.stacks.docker-socket-proxy.enable
Declared by:
nps.stacks.homepage.widgets
Homepage widgets configuration.
See https://gethomepage.dev/widgets/.
Type: YAML 1.1 value
Default:
[ ]
Example:
[
{
resources = {
cpu = true;
disk = "/";
memory = true;
};
}
{
search = {
provider = "duckduckgo";
target = "_blank";
};
}
]
Declared by:
nps.stacks.hortusfox.enable
Whether to enable hortusfox.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.hortusfox.adminEmail
E-Mail of the admin user
Type: string
Default:
"admin@example.com"
Declared by:
nps.stacks.hortusfox.adminPasswordFile
Path to the file containing the admin password.
When using proxy auth, this can also be unset
Type: null or absolute path
Default:
null
Declared by:
nps.stacks.hortusfox.containers.hortusfox
Alias of services.podman.containers.hortusfox.
Type: submodule
Declared by:
nps.stacks.hortusfox.containers.hortusfox-db
Alias of services.podman.containers.hortusfox-db.
Type: submodule
Declared by:
nps.stacks.hortusfox.db.rootPasswordFile
Path to the file containing the password for the MariaDB root user
Type: absolute path
Declared by:
nps.stacks.hortusfox.db.userPasswordFile
Path to the file containing the password for the romm database user
Type: absolute path
Declared by:
nps.stacks.hortusfox.extraEnv
Extra environment variables to set for the container.
See https://github.com/danielbrendel/hortusfox-web?tab=readme-ov-file#installation
Type: attribute set of (null or boolean or signed integer or string or absolute path or (submodule))
Default:
{ }
Example:
{
PROXY_ENABLE = true;
PROXY_HEADER_EMAIL = "Remote-Email";
PROXY_HEADER_USERNAME = "Remote-User";
PROXY_AUTO_SIGNUP = true;
PROXY_WHITELIST = config.nps.stacks.traefik.ip4;
PROXY_HIDE_LOGOUT = true;
}
Declared by:
nps.stacks.immich.enable
Whether to enable immich.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.immich.containers.immich
Alias of services.podman.containers.immich.
Type: submodule
Declared by:
nps.stacks.immich.containers.immich-db
Alias of services.podman.containers.immich-db.
Type: submodule
Declared by:
nps.stacks.immich.containers.immich-machine-learning
Alias of services.podman.containers.immich-machine-learning.
Type: submodule
Declared by:
nps.stacks.immich.containers.immich-redis
Alias of services.podman.containers.immich-redis.
Type: submodule
Declared by:
nps.stacks.immich.dbPasswordFile
Path to the file containing the PostgreSQL password for the Immich database.
Type: absolute path
Declared by:
nps.stacks.immich.oidc.enable
Whether to enable OIDC login with Authelia. This will register an OIDC client in Authelia and setup the necessary configuration in Immich.
For details, see:
- https://www.authelia.com/integration/openid-connect/clients/immich/
- https://immich.app/docs/administration/oauth/
Type: boolean
Default:
false
Declared by:
nps.stacks.immich.oidc.adminGroup
Users of this group will be assigned admin rights in Immich. The role is only used on user creation and not synchronized after that.
See https://immich.app/docs/administration/oauth/
Type: string
Default:
"immich_admin"
Declared by:
nps.stacks.immich.oidc.clientSecretFile
Path to the file containing that client secret that will be used to authenticate against Authelia.
Type: absolute path
Declared by:
nps.stacks.immich.oidc.clientSecretHash
The hashed client_secret. Will be set in the Authelia client config. For examples on how to generate a client secret, see
https://www.authelia.com/integration/openid-connect/frequently-asked-questions/#client-secret
Type: string
Declared by:
nps.stacks.immich.oidc.userGroup
Users of this group will be able to log in to Immich
Type: string
Default:
"immich_user"
Declared by:
nps.stacks.immich.settings
Settings that will be written to the ‘config.json’ file.
If you want to configure settings through the UI, set this option to null.
In that case, no managed config.json will be provided.
For details to the config file see https://immich.app/docs/install/config-file/
Type: null or JSON value
Declared by:
nps.stacks.ittools.enable
Whether to enable ittools.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.ittools.containers.ittools
Alias of services.podman.containers.ittools.
Type: submodule
Declared by:
nps.stacks.karakeep.enable
Whether to enable karakeep.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.karakeep.containers.karakeep
Alias of services.podman.containers.karakeep.
Type: submodule
Declared by:
nps.stacks.karakeep.containers.karakeep-chrome
Alias of services.podman.containers.karakeep-chrome.
Type: submodule
Declared by:
nps.stacks.karakeep.containers.karakeep-meilisearch
Alias of services.podman.containers.karakeep-meilisearch.
Type: submodule
Declared by:
nps.stacks.karakeep.meiliMasterKeyFile
Path to file containing the MEILI_MASTER_KEY
See https://docs.karakeep.app/configuration/
Type: absolute path
Declared by:
nps.stacks.karakeep.nextauthSecretFile
Path to file containing the NEXTAUTH_SECRET
See https://docs.karakeep.app/configuration/
Type: absolute path
Declared by:
nps.stacks.karakeep.oidc.enable
Whether to enable OIDC login with Authelia. This will register an OIDC client in Authelia and setup the necessary configuration.
For details, see:
- https://www.authelia.com/integration/openid-connect/clients/karakeep/
- https://docs.karakeep.app/configuration/#authentication--signup
Type: boolean
Default:
false
Declared by:
nps.stacks.karakeep.oidc.clientSecretFile
The file containing the client secret for the OIDC client that will be registered in Authelia.
Type: string
Declared by:
nps.stacks.karakeep.oidc.clientSecretHash
The hashed client_secret. Will be set in the Authelia client config. For examples on how to generate a client secret, see
https://www.authelia.com/integration/openid-connect/frequently-asked-questions/#client-secret
Type: string
Declared by:
nps.stacks.karakeep.oidc.userGroup
Users of this group will be able to log in
Type: string
Default:
"karakeep_user"
Declared by:
nps.stacks.kimai.enable
Whether to enable kimai.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.kimai.adminEmail
Email address of the admin user
Type: string
Declared by:
nps.stacks.kimai.adminPasswordFile
Path to the file containing the admin password
Type: absolute path
Declared by:
nps.stacks.kimai.containers.kimai
Alias of services.podman.containers.kimai.
Type: submodule
Declared by:
nps.stacks.kimai.containers.kimai-db
Alias of services.podman.containers.kimai-db.
Type: submodule
Declared by:
nps.stacks.kimai.db.databaseName
Name of the database to use for Kimai.
Type: string
Default:
"kimai"
Declared by:
nps.stacks.kimai.db.rootPasswordFile
Path to the file containing the password for the MySQL root user.
Type: absolute path
Declared by:
nps.stacks.kimai.db.userPasswordFile
Path to the file containing the password for the Kimai database user.
Type: absolute path
Declared by:
nps.stacks.kimai.db.username
Username for the Kimai database user.
Type: string
Default:
"kimai"
Declared by:
nps.stacks.komga.enable
Whether to enable komga.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.komga.containers.komga
Alias of services.podman.containers.komga.
Type: submodule
Declared by:
nps.stacks.komga.oidc.enable
Whether to enable OIDC login with Authelia. This will register an OIDC client in Authelia and setup the necessary configuration.
For details, see:
- https://www.authelia.com/integration/openid-connect/clients/komga/
- https://komga.org/docs/installation/oauth2#advanced-configuration
Type: boolean
Default:
false
Declared by:
nps.stacks.komga.oidc.clientSecretFile
The file containing the client secret for the OIDC client that will be registered in Authelia.
Type: string
Declared by:
nps.stacks.komga.oidc.clientSecretHash
The hashed client_secret. Will be set in the Authelia client config. For examples on how to generate a client secret, see
https://www.authelia.com/integration/openid-connect/frequently-asked-questions/#client-secret
Type: string
Declared by:
nps.stacks.komga.oidc.userGroup
Users must be a part of this group to be able to log in.
Type: string
Default:
"komga_user"
Declared by:
nps.stacks.komga.settings
Additional settings that will be provided as the application.yml file.
See https://komga.org/docs/installation/configuration/
Type: YAML 1.1 value
Default:
{ }
Declared by:
nps.stacks.lldap.enable
Whether to enable lldap.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.lldap.adminPasswordFile
Path to the file containing the admin password.
Type: absolute path
Declared by:
nps.stacks.lldap.adminUsername
Admin username for LDAP as well as the web interface.
Type: string
Default:
"admin"
Declared by:
nps.stacks.lldap.baseDn
The starting point in the LDAP directory tree from which searches begin.
Type: string
Default:
"DC=example,DC=com"
Example:
"DC=mydomain,DC=net"
Declared by:
nps.stacks.lldap.bootstrap.cleanUp
Whether to delete groups and users not specified in the config, also remove users from groups that they do not belong to
Type: boolean
Default:
false
Declared by:
nps.stacks.lldap.bootstrap.groupSchemas
Group schemas. Can be used to create custom group attributes.
Type: attribute set of (submodule)
Default:
{ }
Declared by:
nps.stacks.lldap.bootstrap.groupSchemas.<name>.attributeType
Type of the attribute
Type: one of “STRING”, “INTEGER”, “JPGEG”, “DATE_TIME”
Declared by:
nps.stacks.lldap.bootstrap.groupSchemas.<name>.isEditable
Whether the attribute is editable by users
Type: boolean
Default:
false
Declared by:
nps.stacks.lldap.bootstrap.groupSchemas.<name>.isList
Whether the attribute can have multiple values
Type: boolean
Default:
false
Declared by:
nps.stacks.lldap.bootstrap.groupSchemas.<name>.isVisible
Whether the attribute is visible by users
Type: boolean
Default:
true
Declared by:
nps.stacks.lldap.bootstrap.groupSchemas.<name>.name
Name of field, case insensitve - you should use lowercase
Type: string matching the pattern ^[a-zA-Z0-9-]+$
Default:
<name>
Declared by:
nps.stacks.lldap.bootstrap.groups
Groups that will be created.
Besides the name, you can also specify custom attributes for the group, if they are defined in the groupSchemas option.
Type: attribute set of (string or signed integer or boolean)
Default:
{ }
Declared by:
nps.stacks.lldap.bootstrap.groups.<name>.name
Name of the group. Defaults to the name of the attribute.
Type: string
Default:
<name>
Declared by:
nps.stacks.lldap.bootstrap.userSchemas
User schema. Can be used to create custom user attributes.
Type: attribute set of (submodule)
Default:
{ }
Declared by:
nps.stacks.lldap.bootstrap.userSchemas.<name>.attributeType
Type of the attribute
Type: one of “STRING”, “INTEGER”, “JPGEG”, “DATE_TIME”
Declared by:
nps.stacks.lldap.bootstrap.userSchemas.<name>.isEditable
Whether the attribute is editable by users
Type: boolean
Default:
false
Declared by:
nps.stacks.lldap.bootstrap.userSchemas.<name>.isList
Whether the attribute can have multiple values
Type: boolean
Default:
false
Declared by:
nps.stacks.lldap.bootstrap.userSchemas.<name>.isVisible
Whether the attribute is visible by users
Type: boolean
Default:
true
Declared by:
nps.stacks.lldap.bootstrap.userSchemas.<name>.name
Name of field, case insensitve - you should use lowercase
Type: string matching the pattern ^[a-zA-Z0-9-]+$
Default:
<name>
Declared by:
nps.stacks.lldap.bootstrap.users
LLDAP users that will be provisioned at startup.
You can also specify custom attributes for the user, if they are defined in the useSchemas option.
Type: attribute set of (string or signed integer or boolean)
Default:
{ }
Declared by:
nps.stacks.lldap.bootstrap.users.<name>.avatar_url
Must be a valid URL to jpeg file. (ignored if gravatar_avatar specified)
Type: null or string
Default:
null
Declared by:
nps.stacks.lldap.bootstrap.users.<name>.displayName
Display name of the user
Type: null or string
Default:
null
Declared by:
nps.stacks.lldap.bootstrap.users.<name>.email
E-Mail of the user
Type: string
Declared by:
nps.stacks.lldap.bootstrap.users.<name>.firstName
First name of the user
Type: null or string
Default:
null
Declared by:
nps.stacks.lldap.bootstrap.users.<name>.gravatar_avatar
the script will try to get an avatar from gravatar by previously specified email
Type: boolean
Default:
false
Declared by:
nps.stacks.lldap.bootstrap.users.<name>.groups
An array of groups the user will be a member of (all the groups must be specified in the bootstrap.groups option)
Type: list of string
Default:
[ ]
Declared by:
nps.stacks.lldap.bootstrap.users.<name>.id
ID of the user. Defaults to the name of the attribute.
Type: string
Default:
<name>
Declared by:
nps.stacks.lldap.bootstrap.users.<name>.lastName
Last name of the user
Type: null or string
Default:
null
Declared by:
nps.stacks.lldap.bootstrap.users.<name>.password_file
Path to the file containing the user password
Type: null or absolute path
Default:
null
Declared by:
nps.stacks.lldap.containers.lldap
Alias of services.podman.containers.lldap.
Type: submodule
Declared by:
nps.stacks.lldap.jwtSecretFile
Path to the file containing the JWT secret
Type: absolute path
Declared by:
nps.stacks.lldap.keySeedFile
Path to the file containing the key seed
Type: absolute path
Declared by:
nps.stacks.lldap.settings
Additional lldap configuration.
If provided, will be mounted as lldap_config.toml;
See https://github.com/lldap/lldap/blob/main/lldap_config.docker_template.toml
Type: null or TOML value
Declared by:
nps.stacks.mazanoke.enable
Whether to enable mazanoke.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.mazanoke.containers.mazanoke
Alias of services.podman.containers.mazanoke.
Type: submodule
Declared by:
nps.stacks.mealie.enable
Whether to enable mealie.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.mealie.containers.mealie
Alias of services.podman.containers.mealie.
Type: submodule
Declared by:
nps.stacks.mealie.oidc.enable
Whether to enable OIDC login with Authelia. This will register an OIDC client in Authelia and setup the necessary configuration.
For details, see:
- https://www.authelia.com/integration/openid-connect/clients/mealie/
- https://docs.mealie.io/documentation/getting-started/authentication/oidc-v2/
- https://docs.mealie.io/documentation/getting-started/installation/backend-config/#openid-connect-oidc
Type: boolean
Default:
false
Declared by:
nps.stacks.mealie.oidc.adminGroup
Users of this group will be assigned admin rights
Type: string
Default:
"mealie_admin"
Declared by:
nps.stacks.mealie.oidc.clientSecretFile
The file containing the client secret for the OIDC client that will be registered in Authelia.
Type: string
Declared by:
nps.stacks.mealie.oidc.clientSecretHash
The hashed client_secret. Will be set in the Authelia client config. For examples on how to generate a client secret, see
https://www.authelia.com/integration/openid-connect/frequently-asked-questions/#client-secret
Type: string
Declared by:
nps.stacks.mealie.oidc.userGroup
Users must be a part of this group to be able to log in.
Type: string
Default:
"mealie_user"
Declared by:
nps.stacks.memos.enable
Whether to enable memos.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.memos.containers.memos
Alias of services.podman.containers.memos.
Type: submodule
Declared by:
nps.stacks.memos.containers.memos-db
Alias of services.podman.containers.memos-db.
Type: submodule
Declared by:
nps.stacks.memos.db.passwordFile
The file containing the PostgreSQL password for the database. Only used if db.type is set to “postgres”.
Type: absolute path
Declared by:
nps.stacks.memos.db.type
Type of the database to use.
Can be set to “sqlite” or “postgres”.
If set to “postgres”, the passwordFile option must be set.
Type: one of “sqlite”, “postgres”
Default:
"sqlite"
Declared by:
nps.stacks.memos.db.username
The PostgreSQL user to use for the database. Only used if db.type is set to “postgres”.
Type: string
Default:
"memos"
Declared by:
nps.stacks.memos.oidc.clientSecretHash
The hashed client_secret. For examples on how to generate a client secret, see
https://www.authelia.com/integration/openid-connect/frequently-asked-questions/#client-secret
Type: string
Declared by:
nps.stacks.memos.oidc.registerClient
Whether to register an OIDC client in Authelia.
If enabled you need to provide a hashed secret in the client_secret option.
To enable OIDC Login for Memos, you will have to configure it in the Web UI.
For details, see:
- https://www.authelia.com/integration/openid-connect/clients/memos/
- https://www.usememos.com/docs/configuration/authentication#oauth-sso-providers
Type: boolean
Default:
false
Declared by:
nps.stacks.memos.oidc.userGroup
Users of this group will be able to log in
Type: string
Default:
"memos_user"
Declared by:
nps.stacks.microbin.enable
Whether to enable microbin.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.microbin.containers.microbin
Alias of services.podman.containers.microbin.
Type: submodule
Declared by:
nps.stacks.microbin.extraEnv
Extra environment variables to set for the container. Variables can be either set directly or sourced from a file (e.g. for secrets).
See https://microbin.eu/docs/installation-and-configuration/configuration
Type: attribute set of (null or boolean or signed integer or string or absolute path or (submodule))
Default:
{ }
Declared by:
nps.stacks.monitoring.enable
Enable the monitoring stack. This stack provides monitoring services including Grafana, Loki, Alloy, and Prometheus. Configuration files for each service will be provided automatically to work out of the box.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.monitoring.alertmanager.enable
Whether to enable the Alertmanager.
When setting alertmanager.ntfy.enable, a route and receiver configuration will be setup for ntfy.
If using without ntfy, you will have to provide your own route and receiver configurations via the settings option
for Alertmanager to startup correctly.
Type: boolean
Default:
false
Declared by:
nps.stacks.monitoring.alertmanager.ntfy.enable
Whether to setup and configure alertmanager-ntfy. This allows alerts to be forwarded to ntfy.
See https://github.com/alexbakker/alertmanager-ntfy
Type: boolean
Default:
config.nps.stacks.ntfy.enable
Declared by:
nps.stacks.monitoring.alertmanager.ntfy.settings
alertmanager-ntfy configuration. Will be provided as the config.yml.
See https://github.com/alexbakker/alertmanager-ntfy/pkgs/container/alertmanager-ntfy#configuration
Type: YAML 1.1 value
Default:
{ }
Declared by:
nps.stacks.monitoring.alertmanager.ntfy.tokenFile
Path to the file containing the token that is used for authentication against the ntfy service. Only required if ntfy is configured to require authentication.
Type: null or absolute path
Default:
null
Declared by:
nps.stacks.monitoring.alertmanager.settings
Alertmanager configuration. Will be provided as the alertmanager.yml.
See https://prometheus.io/docs/alerting/latest/configuration/
Type: YAML 1.1 value
Default:
{ }
Declared by:
nps.stacks.monitoring.alloy.enable
Whether to enable Alloy.
Type: boolean
Default:
true
Example:
true
Declared by:
nps.stacks.monitoring.alloy.config
Configuration for Alloy.
A default configuration will be automatically provided by this monitoring module.
The default configuration will ship logs of all containers that set the alloy.enable=true option to Loki.
Multiple definitions of this option will be merged together into a single file.
See https://grafana.com/docs/alloy/latest/get-started/configuration-syntax/
Type: strings concatenated with “\n”
Declared by:
nps.stacks.monitoring.alloy.useSocketProxy
Whether to access the Podman socket through the read-only proxy for the monitoring stack. Will be enabled by default if the ‘docker-socket-proxy’ stack is enabled.
Type: boolean
Default:
config.nps.stacks.docker-socket-proxy.enable
Declared by:
nps.stacks.monitoring.containers.alloy
Alias of services.podman.containers.alloy.
Type: submodule
Declared by:
nps.stacks.monitoring.containers.grafana
Alias of services.podman.containers.grafana.
Type: submodule
Declared by:
nps.stacks.monitoring.containers.loki
Alias of services.podman.containers.loki.
Type: submodule
Declared by:
nps.stacks.monitoring.containers.podman-exporter
Alias of services.podman.containers.podman-exporter.
Type: submodule
Declared by:
nps.stacks.monitoring.containers.prometheus
Alias of services.podman.containers.prometheus.
Type: submodule
Declared by:
nps.stacks.monitoring.grafana.enable
Whether to enable Grafana.
Type: boolean
Default:
true
Example:
true
Declared by:
nps.stacks.monitoring.grafana.dashboards
List of paths to Grafana dashboard JSON files.
Type: list of absolute path
Default:
[ ]
Declared by:
nps.stacks.monitoring.grafana.datasources
Datasource configuration for Grafana. Loki and Prometheus datasources will be automatically configured.
Type: YAML 1.1 value
Declared by:
nps.stacks.monitoring.grafana.oidc.enable
Whether to enable OIDC login with Authelia. This will register an OIDC client in Authelia and setup the necessary configuration.
For details, see:
- https://www.authelia.com/integration/openid-connect/clients/grafana/
- https://docs.mealie.io/documentation/getting-started/authentication/oidc-v2/
- https://docs.mealie.io/documentation/getting-started/installation/backend-config/#openid-connect-oidc
Type: boolean
Default:
false
Declared by:
nps.stacks.monitoring.grafana.oidc.adminGroup
Users of this group will be assigned the Grafana ‘Admin’ role.
Type: string
Default:
"grafana_admin"
Declared by:
nps.stacks.monitoring.grafana.oidc.clientSecretFile
The file containing the client secret for the OIDC client that will be registered in Authelia.
Type: string
Declared by:
nps.stacks.monitoring.grafana.oidc.clientSecretHash
The hashed client_secret. Will be set in the Authelia client config. For examples on how to generate a client secret, see
https://www.authelia.com/integration/openid-connect/frequently-asked-questions/#client-secret
Type: string
Declared by:
nps.stacks.monitoring.grafana.oidc.userGroup
Users of this group will be assigned the Grafana ‘Viewer’ role.
Type: string
Default:
"grafana_user"
Declared by:
nps.stacks.monitoring.grafana.settings
Settings for Grafana. Will be written to the ‘grafana.ini’ file. See https://grafana.com/docs/grafana/latest/setup-grafana/configure-grafana/#configure-grafana
Type: attribute set of section of an INI file (attrs of INI atom (null, bool, int, float or string))
Default:
{ }
Declared by:
nps.stacks.monitoring.loki.enable
Whether to enable Loki.
Type: boolean
Default:
true
Example:
true
Declared by:
nps.stacks.monitoring.loki.config
Configuration for Loki. A default configuration will be automatically provided by this monitoring module.
See https://grafana.com/docs/loki/latest/configuration/
Type: YAML 1.1 value
Default:
{ }
Declared by:
nps.stacks.monitoring.podmanExporter.enable
Whether to enable Podman Metrics Exporter.
Type: boolean
Default:
true
Example:
true
Declared by:
nps.stacks.monitoring.prometheus.enable
Whether to enable Prometheus.
Type: boolean
Default:
true
Example:
true
Declared by:
nps.stacks.monitoring.prometheus.rules
Alerting rule configuration for Prometheus.
If provided, the rules will added to the rule_file setting.
See https://prometheus.io/docs/prometheus/latest/configuration/alerting_rules/
Type: YAML 1.1 value
Default:
{ }
Declared by:
nps.stacks.monitoring.prometheus.settings
Configuration for Prometheus. A default configuration will be automatically provided by this monitoring module.
See https://prometheus.io/docs/prometheus/latest/configuration/configuration/
Type: YAML 1.1 value
Default:
{ }
Declared by:
nps.stacks.n8n.enable
Whether to enable n8n.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.n8n.containers.n8n
Alias of services.podman.containers.n8n.
Type: submodule
Declared by:
nps.stacks.networking-toolbox.enable
Whether to enable networking-toolbox.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.networking-toolbox.containers.networking-toolbox
Alias of services.podman.containers.networking-toolbox.
Type: submodule
Declared by:
nps.stacks.ntfy.enable
Whether to enable ntfy.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.ntfy.enableGrafanaDashboard
Whether to enable Grafana Dashboard.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.ntfy.enablePrometheusExport
Whether to enable Prometheus Export.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.ntfy.containers.ntfy
Alias of services.podman.containers.ntfy.
Type: submodule
Declared by:
nps.stacks.ntfy.extraEnv
Extra environment variables to set for the container. Variables can be either set directly or sourced from a file (e.g. for secrets).
For example in order to enable web push support, make sure you pass the ‘NTFY_WEB_PUSH_PUBLIC_KEY’,
‘NTFY_WEB_PUSH_PRIVATE_KEY’ & ‘NTFY_WEB_PUSH_EMAIL_ADDRESS’ variables.
Keys can be generated by running podman run --rm docker.io/binwiederhier/ntfy:latest webpush keys
Type: attribute set of (null or boolean or signed integer or string or absolute path or (submodule))
Declared by:
nps.stacks.ntfy.settings
Server configuration (alternative to environment variable based configuration).
Will be mounted as /etc/ntfy/server.yml in the container.
The final configuration file will be templated with gomplate, so secrets can be read from files or environment variables.
See
- https://docs.ntfy.sh/config/#config-options
- https://docs.ntfy.sh/config/#configuring-the-ntfy-server
- https://github.com/binwiederhier/ntfy/blob/main/server/server.yml
Type: YAML 1.1 value
Default:
{ }
Example:
{
auth-default-access = "deny-all";
enable-login = true;
web-push-private-key = "{{ file.Read `/run/secrets/web_push_private_key` }}";
}
Declared by:
nps.stacks.omnitools.enable
Whether to enable omnitools.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.omnitools.containers.omnitools
Alias of services.podman.containers.omnitools.
Type: submodule
Declared by:
nps.stacks.outline.enable
Whether to enable outline.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.outline.containers.outline
Alias of services.podman.containers.outline.
Type: submodule
Declared by:
nps.stacks.outline.containers.outline-db
Alias of services.podman.containers.outline-db.
Type: submodule
Declared by:
nps.stacks.outline.db.passwordFile
Path to the file containing the database password
Type: absolute path
Declared by:
nps.stacks.outline.db.username
Database user name
Type: string
Default:
"outline"
Declared by:
nps.stacks.outline.extraEnv
Extra environment variables to set for the container.
Can be used to pass secrets such as the TMDB_ACCESS_TOKEN.
See https://github.com/outline/outline/blob/main/.env.sample
Type: attribute set of (null or boolean or signed integer or string or absolute path or (submodule))
Default:
{ }
Example:
{
DEFAULT_LANGUAGE = "en_US";
TMDB_ACCESS_TOKEN = {
fromFile = "/run/secrets/tmdb_access_token";
};
}
Declared by:
nps.stacks.outline.oidc.enable
Whether to enable OIDC login with Authelia. This will register an OIDC client in Authelia and setup the necessary configuration.
For details, see:
- https://www.authelia.com/integration/openid-connect/clients/outline/
- https://docs.getoutline.com/s/hosting/doc/oidc-8CPBm6uC0I
Type: boolean
Default:
false
Declared by:
nps.stacks.outline.oidc.clientSecretFile
The file containing the client secret for the OIDC client that will be registered in Authelia.
Type: string
Declared by:
nps.stacks.outline.oidc.clientSecretHash
The hashed client_secret. Will be set in the Authelia client config. For examples on how to generate a client secret, see
https://www.authelia.com/integration/openid-connect/frequently-asked-questions/#client-secret
Type: string
Declared by:
nps.stacks.outline.oidc.userGroup
Users of this group will be able to log in
Type: string
Default:
"outline_user"
Declared by:
nps.stacks.outline.secretKeyFile
Path to the file containing the secret key.
Can be generated using openssl rand -hex 32
See https://github.com/outline/outline/blob/main/.env.sample
Type: absolute path
Declared by:
nps.stacks.outline.utilsSecretFile
Path to the file containing the utils secret.
Can be generated using openssl rand -hex 32
See https://github.com/outline/outline/blob/main/.env.sample
Type: absolute path
Declared by:
nps.stacks.paperless.enable
Whether to enable paperless.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.paperless.adminProvisioning.enable
Whether to automatically create an admin user on the first run.
If set to false, an admin user can be manually created using the createsuperuser command.
See https://docs.paperless-ngx.com/administration/#create-superuser
Type: boolean
Default:
true
Declared by:
nps.stacks.paperless.adminProvisioning.email
Email address for the admin user
Type: string
Declared by:
nps.stacks.paperless.adminProvisioning.passwordFile
Path to a file containing the admin user password
Type: absolute path
Default:
null
Declared by:
nps.stacks.paperless.adminProvisioning.username
Username for the admin user
Type: string
Default:
"admin"
Declared by:
nps.stacks.paperless.containers.paperless
Alias of services.podman.containers.paperless.
Type: submodule
Declared by:
nps.stacks.paperless.containers.paperless-broker
Alias of services.podman.containers.paperless-broker.
Type: submodule
Declared by:
nps.stacks.paperless.containers.paperless-db
Alias of services.podman.containers.paperless-db.
Type: submodule
Declared by:
nps.stacks.paperless.containers.paperless-ftp
Alias of services.podman.containers.paperless-ftp.
Type: submodule
Declared by:
nps.stacks.paperless.db.passwordFile
Path to the file containing the database password for Paperless
Type: absolute path
Declared by:
nps.stacks.paperless.db.username
Database user name for Paperless
Type: string
Default:
"paperless"
Declared by:
nps.stacks.paperless.extraEnv
Extra environment variables to set for the container. Variables can be either set directly or sourced from a file (e.g. for secrets).
See https://docs.paperless-ngx.com/configuration
Type: attribute set of (null or boolean or signed integer or string or absolute path or (submodule))
Default:
{ }
Declared by:
nps.stacks.paperless.ftp.enable
Whether to enable FTP server.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.paperless.ftp.passwordFile
Path to the file containing the FTP password
Type: absolute path
Declared by:
nps.stacks.paperless.oidc.enable
Whether to enable OIDC login with Authelia. This will register an OIDC client in Authelia and setup the necessary configuration for Paperless.
For details, see:
For details, see:
- https://www.authelia.com/integration/openid-connect/clients/paperless/
- https://docs.paperless-ngx.com/advanced_usage/#openid-connect-and-social-authentication
Type: boolean
Default:
false
Declared by:
nps.stacks.paperless.oidc.clientSecretFile
The file containing the client secret for the Paperless OIDC client that will be registered in Authelia.
Type: string
Declared by:
nps.stacks.paperless.oidc.clientSecretHash
The hashed client_secret. For examples on how to generate a client secret, see
https://www.authelia.com/integration/openid-connect/frequently-asked-questions/#client-secret
Type: string
Declared by:
nps.stacks.paperless.oidc.userGroup
Users of this group will be able to log in
Type: string
Default:
"paperless_user"
Declared by:
nps.stacks.paperless.secretKeyFile
Path to the file containing the Paperless secret key
See https://docs.paperless-ngx.com/configuration/#PAPERLESS_SECRET_KEY
Type: absolute path
Declared by:
nps.stacks.pocketid.enable
Whether to enable pocketid.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.pocketid.containers.pocketid
Alias of services.podman.containers.pocketid.
Type: submodule
Declared by:
nps.stacks.pocketid.env
Additional environment variables passed to the Pocket ID container See https://pocket-id.org/docs/configuration/environment-variables
Type: unspecified value
Default:
{ }
Declared by:
nps.stacks.pocketid.extraEnv
Extra environment variables to set for the container. Variables can be either set directly or sourced from a file (e.g. for secrets).
See https://pocket-id.org/docs/configuration/environment-variables
Type: attribute set of (null or boolean or signed integer or string or absolute path or (submodule))
Default:
{ }
Example:
{
FOO = "bar";
MAXMIND_LICENSE_KEY = {
fromFile = "/run/secrets/maxmind_key";
};
}
Declared by:
nps.stacks.pocketid.ldap.enableSynchronisation
Whether to sync users and groups from an the LDAP server. Requires the LLDAP stack to be enabled.
Type: boolean
Default:
config.nps.stacks.lldap.enable
Declared by:
nps.stacks.pocketid.ldap.passwordFile
The password for the LDAP user that is used when connecting to the LDAP backend.
Type: absolute path
Default:
config.nps.stacks.lldap.adminPasswordFile
Declared by:
nps.stacks.pocketid.ldap.username
The username that will be used when binding to the LDAP backend.
Type: string
Default:
config.nps.stacks.lldap.adminUsername
Declared by:
nps.stacks.pocketid.traefikIntegration.enable
Whether to setup a pocketid middleware in Traefik.
The middleware will use the https://github.com/sevensolutions/traefik-oidc-auth plugin to secure upstream services.
Type: boolean
Default:
config.nps.stacks.traefik.enable
Declared by:
nps.stacks.pocketid.traefikIntegration.clientId
The client ID used by the Traefik OIDC middleware.
Type: string
Example:
"traefik"
Declared by:
nps.stacks.pocketid.traefikIntegration.clientSecretFile
The file containing the client secret used by the Traefik OIDC middleware.
Type: absolute path
Declared by:
nps.stacks.pocketid.traefikIntegration.encryptionSecretFile
The file containing the encryption secret used by the Traefik OIDC middleware. This should be a random secret.
See https://traefik-oidc-auth.sevensolutions.cc/docs/getting-started/middleware-configuration
Type: absolute path
Declared by:
nps.stacks.romm.enable
Whether to enable romm.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.romm.adminProvisioning.enable
Whether to automatically create an admin user on the first run. If set to false, you will be prompted to create an admin user when visiting the web ui.
Type: boolean
Default:
true
Declared by:
nps.stacks.romm.adminProvisioning.email
Email address for the admin user
Type: string
Declared by:
nps.stacks.romm.adminProvisioning.passwordFile
Path to a file containing the admin user password
Type: absolute path
Declared by:
nps.stacks.romm.adminProvisioning.username
Username for the admin user
Type: string
Default:
"admin"
Declared by:
nps.stacks.romm.authSecretKeyFile
Path to the file containing the random secret key.
Can be generated with openssl rand -hex 32.
Type: absolute path
Declared by:
nps.stacks.romm.containers.romm
Alias of services.podman.containers.romm.
Type: submodule
Declared by:
nps.stacks.romm.containers.romm-db
Alias of services.podman.containers.romm-db.
Type: submodule
Declared by:
nps.stacks.romm.db.rootPasswordFile
Path to the file containing the password for the MariaDB root user
Type: absolute path
Declared by:
nps.stacks.romm.db.userPasswordFile
Path to the file containing the password for the romm database user
Type: absolute path
Declared by:
nps.stacks.romm.extraEnv
Extra environment variables to set for the container. Variables can be either set directly or sourced from a file (e.g. for secrets).
See https://docs.romm.app/latest/Getting-Started/Environment-Variables/
Type: attribute set of (null or boolean or signed integer or string or absolute path or (submodule))
Default:
{ }
Example:
{
IGDB_CLIENT_SECRET = {
fromFile = "/run/secrets/igdb_client_secret";
};
UPLOAD_TIMEOUT = 900;
}
Declared by:
nps.stacks.romm.igir.enable
Whether to install a helper program igir-romm-cleanup that can organize your ROM collection.
Will setup defaults for dat, input & output dirs based on the configured library location.
Also adds parameters to copy remaining (undetected) ROMs as well as grouping multi-disk games.
See
Type: boolean
Default:
false
Declared by:
nps.stacks.romm.igir.package
The igir package to use.
Type: package
Default:
pkgs.igir
Declared by:
nps.stacks.romm.oidc.enable
Whether to enable OIDC login with Authelia. This will register an OIDC client in Authelia and setup the necessary environment variables in RomM.
For details, see:
- https://www.authelia.com/integration/openid-connect/clients/romm/
- https://docs.romm.app/latest/OIDC-Guides/OIDC-Setup-With-Authelia/
Type: boolean
Default:
false
Declared by:
nps.stacks.romm.oidc.adminGroup
Users of this group will be able to log in
Type: string
Default:
"romm_admin"
Declared by:
nps.stacks.romm.oidc.clientSecretFile
Path to the file containing that client secret that will be used by RomM to authenticate against Authelia.
Type: absolute path
Declared by:
nps.stacks.romm.oidc.clientSecretHash
The hashed client_secret. Will be set in the Authelia client config. For examples on how to generate a client secret, see
https://www.authelia.com/integration/openid-connect/frequently-asked-questions/#client-secret
Type: string
Declared by:
nps.stacks.romm.oidc.editorGroup
Users of this group will be assigned the ‘editor’ role
Type: string
Default:
"romm_editor"
Declared by:
nps.stacks.romm.oidc.viewerGroup
Users of this group will assigned the ‘viewer’ role
Type: string
Default:
"romm_viewer"
Declared by:
nps.stacks.romm.romLibraryPath
Base path on the host where the rom library is stored.
Type: absolute path not in the Nix store
Default:
"${config.nps.storageBaseDir}/romm/library"
Example:
"${config.nps.externalStorageBaseDir}/romm/library"
Declared by:
nps.stacks.romm.settings
RomM settings. Will be mounted as the config.yml.
See https://docs.romm.app/latest/Getting-Started/Configuration-File/
Type: YAML 1.1 value
Default:
{ }
Example:
{
platforms = {
gc = "ngc";
psx = "ps";
};
}
Declared by:
nps.stacks.sshwifty.enable
Whether to enable sshwifty.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.sshwifty.containers.sshwifty
Alias of services.podman.containers.sshwifty.
Type: submodule
Declared by:
nps.stacks.sshwifty.settings
Configuration settings that will be mounted as the sshwifty.conf.json file.
The final configuration file will be templated with gomplate, so secrets can be read from files or environment variables for example.
See https://github.com/nirui/sshwifty?tab=readme-ov-file#configuration
Type: null or JSON value
Default:
{ }
Example:
{
SharedKey = "{{ file.Read `/run/secrets/web_password`}}";
}
Declared by:
nps.stacks.stirling-pdf.enable
Whether to enable stirling-pdf.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.stirling-pdf.containers.stirling-pdf
Alias of services.podman.containers.stirling-pdf.
Type: submodule
Declared by:
nps.stacks.storyteller.enable
Whether to enable storyteller.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.storyteller.containers.storyteller
Alias of services.podman.containers.storyteller.
Type: submodule
Declared by:
nps.stacks.storyteller.oidc.enable
Whether to enable OIDC login with Authelia. This will register an OIDC client in Authelia and insert the necessary configuration records into the database.
For details, see:
Type: boolean
Default:
false
Declared by:
nps.stacks.storyteller.oidc.clientSecretFile
The file containing the client secret for the OIDC client that will be registered in Authelia.
Type: string
Declared by:
nps.stacks.storyteller.oidc.clientSecretHash
The hashed client_secret. For examples on how to generate a client secret, see
https://www.authelia.com/integration/openid-connect/frequently-asked-questions/#client-secret
Type: string
Declared by:
nps.stacks.storyteller.oidc.userGroup
Users of this group will be able to log in
Type: string
Default:
"storyteller_user"
Declared by:
nps.stacks.storyteller.secretKeyFile
Path to the file containing the secret key.
See https://storyteller-platform.gitlab.io/storyteller/docs/intro/getting-started#secrets
Type: absolute path
Declared by:
nps.stacks.streaming.enable
Whether to enable streaming.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.streaming.bazarr.enable
Whether to enable bazarr.
Type: boolean
Default:
true
Example:
true
Declared by:
nps.stacks.streaming.bazarr.extraEnv
Extra environment variables to set for the container. Variables can be either set directly or sourced from a file (e.g. for secrets).
Type: attribute set of (null or boolean or signed integer or string or absolute path or (submodule))
Default:
{ }
Declared by:
nps.stacks.streaming.containers.bazarr
Alias of services.podman.containers.bazarr.
Type: submodule
Declared by:
nps.stacks.streaming.containers.gluetun
Alias of services.podman.containers.gluetun.
Type: submodule
Declared by:
nps.stacks.streaming.containers.jellyfin
Alias of services.podman.containers.jellyfin.
Type: submodule
Declared by:
nps.stacks.streaming.containers.prowlarr
Alias of services.podman.containers.prowlarr.
Type: submodule
Declared by:
nps.stacks.streaming.containers.qbittorrent
Alias of services.podman.containers.qbittorrent.
Type: submodule
Declared by:
nps.stacks.streaming.containers.radarr
Alias of services.podman.containers.radarr.
Type: submodule
Declared by:
nps.stacks.streaming.containers.sonarr
Alias of services.podman.containers.sonarr.
Type: submodule
Declared by:
nps.stacks.streaming.flaresolverr.enable
Whether to enable Flaresolverr.
Type: boolean
Default:
true
Example:
true
Declared by:
nps.stacks.streaming.gluetun.enable
Whether to enable Gluetun.
Type: boolean
Default:
true
Example:
true
Declared by:
nps.stacks.streaming.gluetun.extraEnv
Extra environment variables to set for the container. Variables can be either set directly or sourced from a file (e.g. for secrets).
See https://github.com/qdm12/gluetun-wiki/tree/main/setup/options
Type: attribute set of (null or boolean or signed integer or string or absolute path or (submodule))
Default:
{ }
Example:
{
HTTPPROXY_PASSWORD = {
fromFile = "/run/secrets/http_proxy_password";
};
HTTP_CONTROL_SERVER_LOG = "off";
SERVER_NAMES = "Alderamin,Alderamin";
}
Declared by:
nps.stacks.streaming.gluetun.settings
Additional Gluetun configuration settings.
Type: TOML value
Declared by:
nps.stacks.streaming.gluetun.vpnProvider
The VPN provider to use with Gluetun.
Type: string
Declared by:
nps.stacks.streaming.gluetun.wireguardAddressesFile
Path to the file containing the Wireguard addresses. Will be used to set the WIREGUARD_ADDRESSES environment variable.
Type: null or absolute path
Default:
null
Declared by:
nps.stacks.streaming.gluetun.wireguardPresharedKeyFile
Path to the file containing the Wireguard pre-shared key. Will be used to set the WIREGUARD_PRESHARED_KEY environment variable.
Type: null or absolute path
Default:
null
Declared by:
nps.stacks.streaming.gluetun.wireguardPrivateKeyFile
Path to the file containing the Wireguard private key. Will be used to set the WIREGUARD_PRIVATE_KEY environment variable.
Type: absolute path
Declared by:
nps.stacks.streaming.jellyfin.enable
Whether to enable Jellyfin.
Type: boolean
Default:
true
Example:
true
Declared by:
nps.stacks.streaming.jellyfin.oidc.enable
Whether to enable OIDC login with Authelia. This will register an OIDC client in Authelia and setup the necessary configuration file.
The plugin configuration will be automatically provided, the plugin itself has to be installed in the Jellyfin Web-UI tho.
For details, see:
- https://www.authelia.com/integration/openid-connect/clients/jellyfin/
- https://github.com/9p4/jellyfin-plugin-sso
Type: boolean
Default:
false
Declared by:
nps.stacks.streaming.jellyfin.oidc.adminGroup
Users of this group will be assigned admin rights in Jellyfin
Type: string
Default:
"jellyfin_admin"
Declared by:
nps.stacks.streaming.jellyfin.oidc.clientSecretFile
The file containing the client secret for the OIDC client that will be registered in Authelia.
Type: string
Declared by:
nps.stacks.streaming.jellyfin.oidc.clientSecretHash
The hashed client_secret. Will be set in the Authelia client config. For examples on how to generate a client secret, see
https://www.authelia.com/integration/openid-connect/frequently-asked-questions/#client-secret
Type: string
Declared by:
nps.stacks.streaming.jellyfin.oidc.userGroup
Users of this group will be able to log in
Type: string
Default:
"jellyfin_user"
Declared by:
nps.stacks.streaming.prowlarr.enable
Whether to enable prowlarr.
Type: boolean
Default:
true
Example:
true
Declared by:
nps.stacks.streaming.prowlarr.extraEnv
Extra environment variables to set for the container. Variables can be either set directly or sourced from a file (e.g. for secrets).
Type: attribute set of (null or boolean or signed integer or string or absolute path or (submodule))
Default:
{ }
Declared by:
nps.stacks.streaming.qbittorrent.enable
Whether to enable qBittorrent.
Type: boolean
Default:
true
Example:
true
Declared by:
nps.stacks.streaming.qbittorrent.extraEnv
Extra environment variables to set for the container. Variables can be either set directly or sourced from a file (e.g. for secrets).
See https://docs.linuxserver.io/images/docker-qbittorrent/#environment-variables-e
Type: attribute set of (null or boolean or signed integer or string or absolute path or (submodule))
Default:
{ }
Example:
{
TORRENTING_PORT = "6881";
}
Declared by:
nps.stacks.streaming.radarr.enable
Whether to enable radarr.
Type: boolean
Default:
true
Example:
true
Declared by:
nps.stacks.streaming.radarr.extraEnv
Extra environment variables to set for the container. Variables can be either set directly or sourced from a file (e.g. for secrets).
Type: attribute set of (null or boolean or signed integer or string or absolute path or (submodule))
Default:
{ }
Declared by:
nps.stacks.streaming.sonarr.enable
Whether to enable sonarr.
Type: boolean
Default:
true
Example:
true
Declared by:
nps.stacks.streaming.sonarr.extraEnv
Extra environment variables to set for the container. Variables can be either set directly or sourced from a file (e.g. for secrets).
Type: attribute set of (null or boolean or signed integer or string or absolute path or (submodule))
Default:
{ }
Declared by:
nps.stacks.timetracker.enable
Whether to enable timetracker.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.timetracker.containers.timetracker
Alias of services.podman.containers.timetracker.
Type: submodule
Declared by:
nps.stacks.timetracker.db.passwordFile
The file containing the PostgreSQL password for the database. Only used if db.type is set to “postgres”.
Type: absolute path
Declared by:
nps.stacks.timetracker.db.type
Type of the database to use.
Can be set to “sqlite” or “postgres”.
If set to “postgres”, the passwordFile option must be set.
Type: value “postgres” (singular enum)
Default:
"postgres"
Declared by:
nps.stacks.timetracker.db.username
The PostgreSQL user to use for the database. Only used if db.type is set to “postgres”.
Type: string
Default:
"timetracker"
Declared by:
nps.stacks.timetracker.oidc.enable
Whether to enable OIDC login with Authelia. This will register an OIDC client in Authelia and setup the necessary configuration.
For details, see:
- https://github.com/DRYTRIX/TimeTracker/blob/main/docs/OIDC_SETUP.md
Type: boolean
Default:
false
Declared by:
nps.stacks.timetracker.oidc.adminGroup
Users of this group will be assigned admin rights
Type: string
Default:
"timetracker_admin"
Declared by:
nps.stacks.timetracker.oidc.clientSecretFile
The file containing the client secret for the OIDC client that will be registered in Authelia.
Type: string
Declared by:
nps.stacks.timetracker.oidc.clientSecretHash
The hashed client_secret. Will be set in the Authelia client config. For examples on how to generate a client secret, see
https://www.authelia.com/integration/openid-connect/frequently-asked-questions/#client-secret
Type: string
Declared by:
nps.stacks.timetracker.oidc.userGroup
Users of this group will be able to log in
Type: string
Default:
"timetracker_user"
Declared by:
nps.stacks.timetracker.secretKeyFile
Path to the file containing the secret key for flask
Type: absolute path
Declared by:
nps.stacks.traefik.enable
Wheter to enable Traefik. The Traefik stack ships preconfigured with a dynamic and static configuration.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.traefik.enableGrafanaAccessLogDashboard
Whether to enable Grafana Access Log Dashboard.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.traefik.enableGrafanaMetricsDashboard
Whether to enable Grafana Metrics Dashboard.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.traefik.enablePrometheusExport
Whether to enable Prometheus Export.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.traefik.containers.traefik
Alias of services.podman.containers.traefik.
Type: submodule
Declared by:
nps.stacks.traefik.crowdsec.enableLogCollection
Whether logs from Traefik should be collected by CrowdSec. Enabling this will configure the acquis settings for CrowdSec.
Type: boolean
Default:
config.nps.stacks.crowdsec.enable
Declared by:
nps.stacks.traefik.crowdsec.middleware.enable
Whether to setup a Traefik middleware.
Make sure to also configure the bouncerKeyFile option.
Type: boolean
Default:
config.nps.stacks.crowdsec.enable
Declared by:
nps.stacks.traefik.crowdsec.middleware.bouncerKeyFile
Path to the file containing the key for the Traefik bouncer.
If this is set, a Bouncer will be setup in CrowdSec. Also a new crowdsec middleware will be registered in Traefik and added to the public chain.
This will block requests to exposed services that are detected as malicious by Crowdsec.
Type: null or absolute path
Default:
null
Declared by:
nps.stacks.traefik.domain
Base domain handled by Traefik
Type: string
Declared by:
nps.stacks.traefik.dynamicConfig
Dynamic configuration for Traefik.
By default, the module will setup two middlewares: private & public.
The private middleware (applied by default to all services) will only allow access from internal networks.
The public middleware will allow access from the internet. It will be configured
with a rate limit, security headers and a geoblock plugin (if enabled). If enabled, Crowdsec will also
be added to the public middleware chain.
Type: YAML 1.1 value
Default:
{ }
Declared by:
nps.stacks.traefik.extraEnv
Extra environment variables to set for the container. Variables can be either set directly or sourced from a file (e.g. for secrets).
Type: attribute set of (null or boolean or signed integer or string or absolute path or (submodule))
Default:
{ }
Example:
{
CF_DNS_API_TOKEN = {
fromFile = "/run/secrets/secret_name";
};
TRAEFIK_LOG_LEVEL = "ERROR";
}
Declared by:
nps.stacks.traefik.geoblock.enable
Enable the geoblock plugin for Traefik.
This will block access to the services based on the country code of the request.
The plugin uses the IP2Location database to determine the country code.
If enabled, the geoblock will be used in the public middleware,
allowing only requests from the allowed countries.
Type: boolean
Default:
true
Declared by:
nps.stacks.traefik.geoblock.allowedCountries
List of allowed country codes (ISO 3166-1 alpha-2 format) See https://en.wikipedia.org/wiki/ISO_3166-1_alpha-2#Officially_assigned_code_elements
Type: list of string
Default:
[ ]
Declared by:
nps.stacks.traefik.network.name
Network name for Podman bridge network. Will be used by the Traefik Docker provider
Type: string
Default:
"traefik-proxy"
Declared by:
nps.stacks.traefik.staticConfig
Static configuration for Traefik.
By default, for the configured domain, a wildcard certificate will be requested from Let’s Encrypt
and used for all services that are registered with Traefik.
By default Cloudflare with DNS challenge will be used to request the certificate.
This requires the ‘CF_DNS_API_TOKEN’ environment variable to be present, e.g. by providing it via the extraEnv option.
The DNS provider as well as any other settings can be overwritten. For an example see https://github.com/Tarow/nix-podman-stacks/blob/main/examples/traefik-dns-provider.nix
Type: YAML 1.1 value
Declared by:
nps.stacks.traefik.useSocketProxy
Whether to access the Podman socket through the read-only proxy for the traefik stack. Will be enabled by default if the ‘docker-socket-proxy’ stack is enabled.
Type: boolean
Default:
config.nps.stacks.docker-socket-proxy.enable
Declared by:
nps.stacks.uptime-kuma.enable
Whether to enable uptime-kuma.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.uptime-kuma.containers.uptime-kuma
Alias of services.podman.containers.uptime-kuma.
Type: submodule
Declared by:
nps.stacks.vaultwarden.enable
Whether to enable vaultwarden.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.vaultwarden.containers.vaultwarden
Alias of services.podman.containers.vaultwarden.
Type: submodule
Declared by:
nps.stacks.vaultwarden.extraEnv
Extra environment variables to set for the container. Variables can be either set directly or sourced from a file (e.g. for secrets).
See https://github.com/dani-garcia/vaultwarden/blob/main/.env.template
Type: attribute set of (null or boolean or signed integer or string or absolute path or (submodule))
Default:
{ }
Example:
{
ADMIN_SESSION_LIFETIME = 30;
ADMIN_TOKEN = {
fromFile = "/run/secrets/vaultwarden_admin_token";
};
}
Declared by:
nps.stacks.vikunja.enable
Whether to enable vikunja.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.vikunja.containers.vikunja
Alias of services.podman.containers.vikunja.
Type: submodule
Declared by:
nps.stacks.vikunja.containers.vikunja-db
Alias of services.podman.containers.vikunja-db.
Type: submodule
Declared by:
nps.stacks.vikunja.db.passwordFile
The file containing the PostgreSQL password for the database. Only used if db.type is set to “postgres”.
Type: absolute path
Declared by:
nps.stacks.vikunja.db.type
Type of the database to use.
Can be set to “sqlite” or “postgres”.
If set to “postgres”, the passwordFile option must be set.
Type: one of “sqlite”, “postgres”
Default:
"sqlite"
Declared by:
nps.stacks.vikunja.db.username
The PostgreSQL user to use for the database. Only used if db.type is set to “postgres”.
Type: string
Default:
"vikunja"
Declared by:
nps.stacks.vikunja.jwtSecretFile
Path to the file containing the JWT secret.
See https://vikunja.io/docs/config-options/#1-service-JWTSecret
Type: absolute path
Declared by:
nps.stacks.vikunja.oidc.enable
Whether to enable OIDC login with Authelia. This will register an OIDC client in Authelia and setup the necessary configuration.
For details, see:
- https://www.authelia.com/integration/openid-connect/clients/vikunja/
- https://vikunja.io/docs/openid/
Type: boolean
Default:
false
Declared by:
nps.stacks.vikunja.oidc.clientSecretFile
The file containing the client secret for the OIDC client that will be registered in Authelia.
Type: string
Declared by:
nps.stacks.vikunja.oidc.clientSecretHash
The hashed client_secret. Will be set in the Authelia client config. For examples on how to generate a client secret, see
https://www.authelia.com/integration/openid-connect/frequently-asked-questions/#client-secret
Type: string
Declared by:
nps.stacks.vikunja.oidc.userGroup
Users of this group will be able to log in
Type: string
Default:
"vikunja_user"
Declared by:
nps.stacks.vikunja.settings
Extra settings being provided as the /etc/vikunja/config.yml file.
See https://vikunja.io/docs/config-options
Type: YAML 1.1 value
Default:
{ }
Declared by:
nps.stacks.webtop.enable
Whether to enable webtop.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.webtop.containers.webtop
Alias of services.podman.containers.webtop.
Type: submodule
Declared by:
nps.stacks.webtop.passwordFile
Password for HTTP Basic Auth. If unset, authentication is disabled.
Type: null or absolute path
Default:
null
Declared by:
nps.stacks.webtop.username
Username for HTTP Basic Auth
Type: string
Default:
"abc"
Declared by:
nps.stacks.wg-easy.enable
Whether to enable wg-easy.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.wg-easy.containers.wg-easy
Alias of services.podman.containers.wg-easy.
Type: submodule
Declared by:
nps.stacks.wg-easy.extraEnv
Extra environment variables to set for the container. Variables can be either set directly or sourced from a file (e.g. for secrets).
See https://wg-easy.github.io/wg-easy/latest/advanced/config/unattended-setup/
Type: attribute set of (null or boolean or signed integer or string or absolute path or (submodule))
Default:
{ }
Example:
{
INIT_DNS = "1.1.1.1";
INIT_PASSWORD = {
fromFile = "/run/secrets/wg_easy_admin_password";
};
}
Declared by:
nps.stacks.wg-easy.host
The external domain or IP address of the Wireguard server. Will be used as the ‘endpoint’ when generating client configurations.
Only has an effect during initial setup. See https://wg-easy.github.io/wg-easy/v15.1/advanced/config/unattended-setup/
Type: string
Default:
"vpn.${config.nps.stacks.traefik.domain}"
Declared by:
nps.stacks.wg-easy.port
The port on which the Wireguard server will listen. Will be passed as INIT_PORT during initial setup. Only has an effect during initial setup. See https://wg-easy.github.io/wg-easy/v15.1/advanced/config/unattended-setup/
Type: 16 bit unsigned integer; between 0 and 65535 (both inclusive)
Default:
51820
Declared by:
nps.stacks.wg-portal.enable
Whether to enable wg-portal.
Type: boolean
Default:
false
Example:
true
Declared by:
nps.stacks.wg-portal.containers.wg-portal
Alias of services.podman.containers.wg-portal.
Type: submodule
Declared by:
nps.stacks.wg-portal.extraEnv
Extra environment variables to set for the container. Variables can be either set directly or sourced from a file (e.g. for secrets).
Can be used to pass secrets or other environment variables that are referenced in the settings.
Type: attribute set of (null or boolean or signed integer or string or absolute path or (submodule))
Default:
{ }
Example:
{
ADMIN_PASSWORD = {
fromFile = "/run/secrets/secret_name";
};
}
Declared by:
nps.stacks.wg-portal.oidc.enable
Whether to enable OIDC login with Authelia. This will register an OIDC client in Authelia and setup the necessary configuration.
For details, see:
- https://wgportal.org/master/documentation/configuration/examples/#openid-connect-oidc-authentication
Type: boolean
Default:
false
Declared by:
nps.stacks.wg-portal.oidc.adminGroup
Users of this group will be assigned admin rights
Type: string
Default:
"wg-portal_admin"
Declared by:
nps.stacks.wg-portal.oidc.clientSecretFile
The file containing the client secret for the OIDC client that will be registered in Authelia.
Type: string
Declared by:
nps.stacks.wg-portal.oidc.clientSecretHash
The hashed client_secret. Will be set in the Authelia client config. For examples on how to generate a client secret, see
https://www.authelia.com/integration/openid-connect/frequently-asked-questions/#client-secret
Type: string
Declared by:
nps.stacks.wg-portal.oidc.userGroup
Users of this group will be able to log in
Type: string
Default:
"wg-portal_user"
Declared by:
nps.stacks.wg-portal.port
The default port for the first Wireguard interface that will be set up in the UI. Will be exposed and passed as the ‘start_listen_port’ setting in the configuration.
Type: 16 bit unsigned integer; between 0 and 65535 (both inclusive)
Default:
51820
Declared by:
nps.stacks.wg-portal.settings
Settings for the wg-portal container. Will be converted to YAML and passed to the container.
See https://wgportal.org/latest/documentation/configuration/overview/
Type: YAML 1.1 value
Example:
{
core = {
admin = {
password = "\${ADMIN_PASSWORD}";
username = "admin";
};
};
}
Declared by:



